
I'm not going to lie to you, this is a little bit technical and also extremely alarming. But I will break it down so that its digestible and actionable. Phishing is when an attacker sends an email that contains a link. When the link is clicked, it will install malicious software, known as malware, onto the target's computer. From there, the attacker will either use the computer to attack other users on the Internet or install ransomware on the victim's computer. Phishing is considered one of the most serious threats to internet users, especially those in more secure environments. In fact, when penetration testers are hired to attempt to break into a target, phishing is often their first mode of attack because its so effective.
You've all mostly like heard of phishing and have probably even received emails with these links in them. In the past, they were very easy to spot because they went to domains you've never heard of. But that is changing now. Now phishing attacks can come from domains that are nearly impossible to distinguish from legitimate ones.
What does a phishing attack look like?
Before continuing, I want to give you a little more information on how a phishing attack works.
A user may receive an email from from an authentic looking email from your bank. The email will details how their bank was attacked by criminal hackers and in order to make sure your accounts are safe, please click this link to be taken to a password rest page. When you click the link, you will be taken to a very legitimate looking page for your bank. You will enter your old password and then a new one to reset it. You complete everything and feel safer, thankful that your bank has alerted you to the threat. But what has really happened is that the hacker has your password and will use it to log into your online banking.
Over the years, the internet using public has become more aware of these attacks and has learned to give the links that they click on a little more scrutiny. The common ways to confuse people were to use numbers to replace letters such is the number 1 for the letter l. An example may be www.apple.com would become www.app1e.com. A casual looker may not notice this slight change and would click the link.
Well a new method makes studying the links almost useless as a defense.
How this new method makes phishing so much more dangerous
The Internet is truly international and as such, domains are now making use of more than just the English letters and numbers. Other languages use different letters and characters to spell out their words. Obvious examples are Arabic, Chinese, Japanese, and Korean. Each of these uses completely different characters in their writing. You can see an example of how this works here (thenextweb.com). You can also learn more about internationalized domain names here (wikipedia.org).
What attackers have done is search through other alphabets and find characters that look virtually identical to those in the English language and then register domains using those letters. To further add credibility to their new scam sites, they will register them for an SSL certificate. That way a user will see the site is encrypted and secure and assume that its legitimate.
Here are some examples:
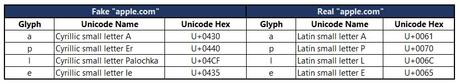
In this example, the Cyrillic alphabet was used to create the fake apple.com domain. Cyrillic is the alphabet used in Russian and other languages. So a Cyrillic small letter A looks nearly identical to an English small letter A. However, since these are different languages, a computer reads them differently. The computer processes each letter based on its Unicode value. We see that the Cyrillic value is U+0430 and the English value is U+0061. So to the computer, they are completely different. But to us humans, they might as well be the same.
Using this technique, an attacker could forge any domain he could match letters from other languages to. That is potentially very scary and makes phishing much more dangerous for small businesses and practices that don't have IT support on site. Being attacked by a phishing email is a potential HIPAA breach. It would also violate PCI-DSS.
If you would like to see this in action, browse over to xn--80ak6aa92e.com I didn't a clickable link because most malware protection will detect it as unsafe. It is safe and there is nothing actually on the site. But when you surf there, you will see the address is apple.com. This is using the unicode letters and is converted by modern browsers to appear as apple.com.
How do we defend ourselves from these types of phishing attacks?
The first thing is that when you are asked to click on a link in an email, instead, open a browser and manually type type the URL. So for example if you received an email from wellsfargo.com, instead of clicking the link in the email, open up your browser and manually type in wellsfargo.com. This is the surest way to protect yourself.
If you use Mozilla, follow these steps to disable this attack from working:
- Open a Mozilla browser window
- Type about:config in address bar and press enter.
- Type Punycode in the search bar.
- You will see the parametercalled: network.IDN_show_punycode, double-click or right-click and select Toggle to change the value from false to True.
- close your browser and Mozilla will no longer be susceptible to these attacks.
Unfortunately, Chrome doesn't have a setting to allow this be disabled.
Another way you can protect yourself is to use a password manager like Lastpass that is integrated with your browser. This way, you can click the site you want to visit in Lastpass and it will open the correct site and enter the passwords. This will keep you from entering your passwords into the the wrong site.
As the internet changes, so do the attacks that are used against us. By learning some basic information, you can go a long way to protecting yourself online. Remember that a phishing attack could well become a much larger breach of security in your business or practice. It is the most common way in for most attackers.

