Cryptocurrency, a form of digital currency that uses cryptography as an extension of security and as a mechanism to control new units’ creation, has been hailed as a natural progression from conventional monetary exchange systems. In today’s world, there are many cryptocurrencies, of which Bitcoin is the most famous. Mining is the process of generating cryptocurrency as a means of validating any transaction.
The process of rapidly producing hashes, which authenticate any transaction, has become more sophisticated due to the development of specialized machines such as FPGAs or ASICs running complex hashing algorithms such as SHA-256 and Scrypt. Thus, cryptocurrency creation has accelerated. Following the launch of Bitcoin, the first cryptocurrency, the quest has been on for affordable, yet more powerful devices ever since. As more and more people become involved with virtual currencies, the process of calculating/obtaining the hashes to validate each transaction becomes more complex as time goes on, resulting in miners investing huge amounts of capital into ASICs that are capable of super-fast transactions.
In other words, the currency received from finding a hash was insufficient to justify the costs related to installing the machines, setting up cooling systems to cope with the heat they generate as well as the electricity needed to run them. This makes it a smart idea to do this via cloud computing. A miner leases supercomputers capable of generating hashes at high rates that are likely to turn a profit, and utilizing the same computer for multiple clients in a time-bound fashion is advantageous for the miners and their cloud providers.
The article delves into the complexities of cryptocurrency mining, the machines traditionally used to mine cryptocurrencies, the flaws of those machines, how cloud mining provides a viable alternative, and the benefits of cloud mining over traditional mining methods.
Also Read: ICO Startup Funding: A Case Study For Entrepreneurs

What Is Mining
The mining process is the primary pathway of generating, transmitting, and validating cryptocurrency transactions. The system ensures smooth, fast, and secure transmission of currency between donors and beneficiaries. Contrary to fiat currencies, which are regulated and controlled by central authorities, cryptocurrencies are decentralized and operate on a peer-to-peer basis. A bank that generates currency and oversees transactions necessitate infrastructural support in order to run effectively. Unlike traditional currencies, crypto assets operate through a mining system in which individuals on the network, known as ‘miners’ or ‘nodes’, are tasked with monitoring and validating transactions in order to produce currency.
A set number of transactions made during a certain period of time are compiled into a ‘Block’. As a method of ensuring a high level of transparency in the currency system, it is structured in such a way that the entire chain of transactions from the time of the creation of the currency is recorded in a general ledger known as ‘Blockchain,’ which is a list of blocks generated in chronological order beginning with the very first block.
In mining, miners are the main players. Miners execute transactions by authenticating ownership of currencies between sources and destinations. Through the hash of the previous transaction, each present transaction is authenticated by testing its authenticity against the previous transaction. In addition to preventing misuse, miners conduct currency validations.
A mining operation’s main objective consists of generating and issuing new coins into the crypto-economy. In the event that a transaction is validated, a miner collects that transaction and adds it to the block that they are working on. Before a block can be broadcast and added to the blockchain, it must first be solved. Solving a block involves solving mathematical puzzles that are difficult to break provided that the output generated has some limitations. In return for solving the puzzle, the block is added to the ledger, and a reward of coins is granted. As a result, mining can be summed up as an algebraic puzzle to solve, and the reward is coins. Keeping this mechanism in place prevents miners from obtaining coins easily, thereby maintaining fairness in the system.
Mining Machines For Cryptocurrencies
To mine cryptocurrency, specialized machines are used called ‘mining machines’. Mining machines have a long history that starts from CPUs and goes all the way to ASICs. With mining’s recurring increase in difficulty, new machines with higher efficiency have been developed over the years. Mining profitability is determined by the cost and performance of mining machines, and the designs and implementations of mining machines play a key role in this. In mining, the following machines are used:
A: CPU
Early on in the history of the mining of the coins, CPUs were used effectively to mine the coins at hash rates lower than or equal to 10MH/sec. In order to complete the mining process, a PC equipped with mining software is sufficient. The constant increase in difficulty in mining has rendered CPUs obsolete in the face of increasingly powerful, high-hash-rate machines. The CPU mining software is known as CPUminer became very popular.
CPuminer is a simple client application for performing pooled mining or solo mining. In this program, block data is received from the server, for which nonce values are determined and a valid block is created. The block data containing the nonce value is returned to the server if the hash of the block has at least 32 consecutive zero bits. As part of Pooled Mining, this block is termed a “share”. This is because the server should credit the registered user’s account after every transaction, based on how many shares they have accumulated, and ultimately send a Bitcoin balance to their account.
B: GPU
CPU mining was not able to keep up with the demand so graphics cards and CPUs were combined to mine the coins. A graphic card contains Graphical Processing Units (GPU), which are used to perform high-level calculations and to render complex polygonal shapes in gaming. In crypto-currencies, hash-proof algorithms are used to solve block transaction blocks requiring high mathematical complexity, and as a result, GPUs began to be considered a viable computer mining alternative.
A CPU core is capable of processing 4 32-bit instructions per clock (using a 128-bit SSE instruction) or 8 through AVX (256-Bit), but GPUs like the AMD Radeon HD 5970 are capable of executing 3200 32-bit operations per clock cycle (using its 3200 ALUs or shaders). A difference of 800 (or 400, if you are using AVX) times more instructions per clock are achieved. The fastest CPUs today have 6, 8, and 12 cores with higher frequency clocks (2000-3000 MHz compared to 725 MHz for the Radeon HD 5970), yet one HD5970 still outperforms four 12-core CPUs at 2.3GHz. The OpenCL miner was released on the web in October 2010 and miners quickly optimized and adapted it. In most cases, miners would implement the SHA protocol in a language like Java or Python, which was then assemble using the GPU’s hidden ISA.
This is because the rigs are left to mine for long periods of time, so the users drastically modify the voltages (lowering them to reduce mining costs, or raising them, with a higher frequency, to increase Gh/s) as well as operating frequencies of video memory (lower since memory is unused) and the GPU itself, along with parameters of the code, like how many threads are enqueued at one time, to optimize performance within reasonable stability and temperature limits. Due to the fact that Bitcoin computation does not rely on a memory system, this means that some cores and components in the GPU are not strained, thus allowing the system to act beyond its normal limits. After a period of time, the parameters of the GPU core become unreliable due to wear in the motherboard fans and power supply systems.
FPGAs are usually more difficult to interface with than GPUs since they need PC-building expertise and a fondness for forum surfing, but no formal expertise in concurrent programming or FPGA tools. With GPUs, BTC hash rates are scaled at unprecedented levels in a way that pushes consumer computing to its limit in innovative and exciting ways. Although GPU has many advantages, they have some drawbacks as well.
Limitations Of GPUs
- Graphics cards can provide up to 800 MH/s, however, they are more expensive than normal CPUs.
- In the absence of GPUs as a standalone, it is not an option. GPUs require PCIe 8x or 16x slots, and commercial motherboards have relatively few of these slots.
- The system components, such as the motherboard, hard drives, and RAM, are not exploited in GPU mining, thus raising the overall cost of mining.
- For GPUs to mine effectively, additional power between 200 and 300 Watts is required.
- In most cases (motherboards), GPUs are available in two slots, preventing users from mounting two or more units in one computer for performance enhancement.
As of today, GPU mining is no longer lucrative and has mostly ceased to exist since the mining difficulty has increased beyond what GPUs can handle. On top of it, the introduction of FPGAs and ASICs into the mining field conferred profitability on mining.
C: FPGA (Field Programmable Gate Array)
FPGAs, Open-source Bitcoin miners were first introduced in June 2011. As mining costs increased in comparison to coins earned from mining, mining profitability was adversely impacted. Because GPU mining has a high mining cost and a low return per day, it was incredibly inefficient. Mining continued to be lucrative for the miners only after the invention of machines which made mining profitable.
In practical terms, FPGAs also referred to as field-programmable gate arrays, are reprogrammable logic IC that can often be configured after manufacture. An FPGA contains individual programmable logic blocks knowns as Configurable Logic Blocks (CLBs). The logic blocks of the system are interconnected in such a way that they may be reconfigured. FPGAs are equipped with lots of logic gates and RAM to perform complex digital computations.
The flexibility and reprogrammability of FPGAs allow a designer to implement any digital function. Considering that FPGAs are more easily synthesized than other cryptographic chips, they make a good Bitcoin mining option. As they are very easily reprogrammable, FPGAs are very reusable.
The use of FPGAs consumes half the energy of GPUs, which has been an issue for GPU mining. The FPGA is also capable of rotating bits-by-constants and bit-level operations, such as those used in the hash-proof SHA256 algorithm used for Bitcoin transactions. An FPGA Mini rig from Butterfly Lab mines about 25,200 MH/s with an efficiency of 20.26 Mhash/J while consuming 1,250Watts of power. GPUs, on the other hand, mine about 800MH/s, on average.
Impedance Limits of FPGAs
- If the volume of production is low, FPGAs are a good choice, as their cost per unit of production rises as the output quantity increases, therefore less economical than its rivals, ASICs.
- BTC FPGAs consume more power than conventional FPGAs, despite being easy to synthesize.
Blockchain Investing – A Beginner’s Guide
D: ASIC (Application Specific Integrated Circuit)
With time, mining coins became increasingly difficult, and mining machines became more affordable, spurring fierce competition among miners for greater profits. FPGAs particularly suited for mining purposes, flexible to program and build, but consume a great deal of power relative to what they offer. As ASICs used for mining became available, they performed better than FPGAs for large-scale mining operations. The advancement of ASIC technology makes sense: ASICs use specially designed circuits to perform hashing at high speed, with minimal power consumption. On the market today, the best ASICs can process significantly more than 1,000 Mhash (1 billion hashes) per joule.
ASICs, or Application Specific Integrated Circuits, are used for a variety of specific applications. It is a microchip built for a specific function, but its applications are potentially endless. Bitcoin ASICs, which are specific to mining Bitcoin, excel at solving complex mathematical problems quickly and efficiently. In spite of FPGA dominance’s short lifespan, it served as an important prelude for ASICs. As compared to FPGA Verilog, ASIC Verilog is similar in its design and implementation
ASICs’ drawbacks are their high price as well as the brisk pace of innovation. This rapid rate at which hardware is improving and achieving higher hash rates than previously designed means that ASIC mining is profitable only for a short time before new, more efficient machines come on the market.
Comparing ASICs to other mining machines, it is clear that ASICs at the moment dominate the mining field, though the future will show how they will hold up with the ever-evolving and better-performing machines.
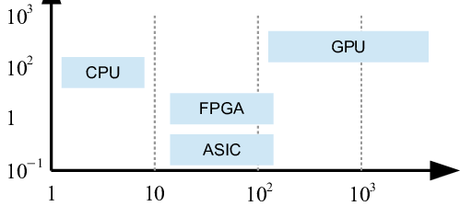
Hardware Comparison Of CPU, GPU, FPGA, and ASICS
In terms of their action and output, mine machines define the whole mining process. In the history of mining, mining profitability and mining difficulty are influenced by the machines used at the respective times. In the following image, BitCoin Network is shown as generating revenue per GH/s.
Bitcoin Mining Profitability
In order to perform Bitcoin mining operations, profitability is an important factor. Factors that determine mining profitability include:
- The hashing speed of the machine
- The initial cost of mining operations such as ASICs
- A measure of how difficult it is to solve currently occurring hashing problems with the network
- Consumption of electricity costs
- Future analysis of Bitcoin’s value
To adopt the traditional mining technique, miners purchase large machines with multiple highly powered ASIC processors. Still, major developments can have a major effect on the price.
BITCOIN DIFFICULTY AND HASH RATE HISTORY (2020-2021)
2021-06-1319,932,791,027,262 - 19.93 T - 5.30 %142.68 EH/s
2021-05-29 21,047,730,572,451 - 21.05 T - 15.97 % 150.48 EH/s
2021-05-13 01:58:5825,046,487,590,083 - 25.05 T + 21.53 % 179.25 EH/s
2021-05-0120,608,845,737,768 - 20.61 T - 12.61 % 147.42 EH/s
2021-04-1523,581,981,443,663 - 23.58 T+ 1.92 %168.79 EH/s
2021-04-01 23,137,439,666,472 - 23.14 T + 5.82 %165.44 EH/s
2021-03-1921,865,558,044,610 - 21.87 T + 1.95 %156.50EH/s
2021-03-05 21,448,277,761,059 - 21.45 T- 1.27 %153.46EH/s
2021-02-19 21,724,134,900,047 - 21.72 T + 1.35 % 155.47 EH/s
2021-02-0521,434,395,961,348 - 21.43 T + 2.93 %153.41 EH/s
2021-01-23 20,823,531,150,111 - 20.82 T+ 1.05 % 149.05 EH/s
2021-01-0920,607,418,304,385 - 20.61 T + 10.79 %147.46 EH/s
2020-12-27 18,599,593,048,299 - 18.60 T - 0.38 %133.13 EH/s
2020-12-1318,670,168,558,399 - 18.67 T - 2.54 %133.54 EH/s
2020-11-29 19,157,154,724,710 - 19.16 T+ 8.87 %137.12 EH/s
2020-11-16 17,596,801,059,571 - 17.60 T + 4.82 %125.96 EH/s
2020-11-03 16,787,779,609,932 - 16.79 T - 16.05 %120.12 EH/s
2020-10-1719,997,335,994,446 - 20.00 T + 3.62 %142.94 EH/s
2020-10-03 19,298,087,186,262 - 19.30 T - 0.09 %138.09 EH/s
2020-09-19 19,314,656,404,097 - 19.31 T + 11.35 %138.09 EH/s
2020-09-0717,345,997,805,929 - 17.35 T - 1.21 %124.12 EH/s
2020-08-2417,557,993,035,167 - 17.56 T + 3.60 %125.59 EH/s
2020-08-1016,947,802,333,946 - 16.95 T + 0.59 %121.27 EH/s
2020-07-2716,847,561,611,550 - 16.85 T - 2.87 %120.57 EH/s
2020-07-13 17,345,948,872,516 - 17.35 T + 9.89 %123.85 EH/s
2020-06-30 15,784,217,546,288 - 15.78 T 0.00%112.84%
2020-06-1615,784,744,305,477 - 15.78 T + 14.95 %112.98 EH/s
2020-06-04 13,732,352,106,018 - 13.73 T - 9.29 %98.30 EH/s
2020-05-19 15,138,043,247,082 - 15.14 T- 6.00 %108.19 EH/s
2020-05-0416,104,807,485,529 - 16.10 T + 0.92 %115.27 EH/s
2020-04-2115,958,652,328,578 - 15.96 T + 8.45 % 114.10 EH/s
2020-04-0814,715,214,060,656 - 14.72 T + 5.77 %105.21 EH/s
2020-03-2513,912,524,048,945 - 13.91 T - 15.95 %99.59 EH/s
2020-03-0916,552,923,967,337 - 16.55 T + 6.88 %118.40 EH/s
020-02-25 15,486,913,440,292 - 15.49 T - 0.38 %110.86 EH/s
2020-02-10 15,546,745,765,529 - 15.55 T + 0.52 %111.23 EH/s
2020-01-28 15,466,098,935,554 - 15.47 T + 4.67 %110.71 EH/s
2020-01-1414,776,367,535,688 - 14.78 T + 7.08 % 105.76 EH/s
2020-01-0113,798,783,827,516 - 13.80 T + 6.57 %98.67 EH/s
What Are The Major Issues In Traditional Mining?
The major problems in traditional mining, commonly referred to as mining are;
-
The problem Of Double-Spending
In this case, the term “double spending” stands for itself. Double spending is a problem that arises when people transact in digital currencies with the same tender being used repeatedly. Digital currencies have a unique problem of double-spending because
The mining of cryptocurrencies is based on Proof of Work (PoW). In order to prevent double-spending, users sign their transactions over the network using a distributed timestamp service. digital data can easily be duplicated, unlike physical currency. The double-spending feature allows a holder of the currency to create a duplicate of it which can then be sent to any merchant or any other party without the original being lost.
Using Bitcoin as an example, it takes on average between 10 and 15 minutes for Bitcoin transactions to finally settle, resulting in inefficiency for fast transactions. Nevertheless, this procedure is imperative in order to identify double-spending. Due to the anonymity and multiple accounts of digital currency users, it is incredibly difficult to track down fraudsters. In response, the Bitcoin developers recognized this issue by proposing a mechanism to allow merchants to submit transactions without waiting for confirmation if the amount of the transaction cannot be outweighed by confirmation.
The proposed solution does not eliminate the theoretical double-spending problem of the network, however, considering that Bitcoins are increasingly used for fast payments, such as at ATMs and for restaurant bills.
In order to identify the factors that could lead to double-spending, it is essential to know the type of payments digital currencies are involved with. In general, the two major payment types are slow and fast payments.
Slow Payments: Slow payment systems are traditional methods of transaction. Normally, slow payments don’t happen until the transaction is confirmed by the network. In the case of confirmed transactions, nefarious attacks will have little chance of succeeding since they are accepted by honest peers. It has been observed that nearly seventy-four percent of all transactions in the Bitcoin network are handled max/min of ten minutes, with the remaining % taking 10-40 minutes to confirm.
Fast Payments: In the case of quick transactions, they cannot be based on the specifications of the transactions, such as shopping centers, ATMs, etc… Fast payments are those where currency and goods are exchanged in a short period of time.
In order to facilitate faster bitcoin transactions, merchants are encouraged to approve transactions without confirming them if the total is not too high. However, the measure cannot prevent the Bitcoin network from being vulnerable.
Conditions For Success On Double-Spending
If double spending is to be successful, the attacker should convince the vendor to accept a TRV (Transaction Request Value) that can’t be subsequently reversed. In this scenario, the attacker creates a transaction (TRa) that contains the same inputs as TRV, however, the recipient address will be one that he controls.
An attacker can achieve success by double-spending if the following conditions are met:
- In circumstances where the vendor’s time to accept the transaction TRV falls short of its acknowledgment time on the transaction TRa. In the absence of a network that supports multiple transactions with the same input, the TRV cannot be redeemed.
- As long as the transaction TRa is already confirmed in another block, the network will not confirm the transaction TRv.
Identifying the Types of Double-Spending Attacks
-
Race Attack
A race attack occurs when the vendor or merchant accepts a 0/unconfirmed transaction immediately. There might have been multiple transactions involving coins in the transaction shown to the merchant that ended up in the block first. Thus, the attacker’s transaction with the merchant is likely to be rejected and the merchant will not be able to reclaim it.
-
Finney Attack
Finney attack is a bogus double-spending practice in which a miner must appear. In the Finney attack, Miners will need to include a non-broadcast in their code. This non-broadcasting transaction aims to accomplish double-spending by deceiving its block generation. For smaller amounts, however, such an attack is insignificant and will not provide any profit.
-
>50% attack
50% attacks are possible when the attacker gains control of over 50% of the network hash rate. This will increase the probability of a fraudulent transaction being confirmed in the network. In order for an attacker to avail himself of such an attack, the profits must be large, but that has become practically impossible with the growth of mining.
In spite of the possibility of double-spending, the possibility of fraud through this method is pretty low. A large portion of today’s fraud is done by malware that attacks wallets present at each node.
-
Malware
The term malware refers to a bot network controlled by hackers that attacks PCs or encrypts data. Malware such as this includes the Trojan-Ransom Trojan.Win32.Linkup cuts off internet access to the computer by modifying DNS settings while turning it into a bot for mining bitcoins. Additionally, to tampering with DNS settings, Linkup is also capable of connecting to remote servers and configuring a PC to act as a Bitcoin miner. The process is accomplished by using a downloader called “pts2.exe”, extracting a second program, known as “j.exe”, on the computer. The program in question is JHProtominer, a widely used mining program.
It is unlikely that the Trojan will cause substantial damage. Unless your operating system is 64-bit, JHProtominer will not work, but nonetheless, there are still plenty of machines around the world that could be affected.
In What Way Does Malware Get Inside Mining Systems?
In addition to arriving as part of a malware package, BKDR_BTMINE.DDOS may also be distributed by IT exploits. Typically it is dropped or downloaded either from malicious sites or by other malware/grayware/spyware programs. Visiting malicious websites can also accidentally prompt users to download these files.
Infecting users’ systems with Bitcoin-mining malware is a common practice among cybercriminals. In one case, they used Tweets containing malicious links to trick users into downloading WORM_KOLAB.SMQX, which then downloaded HKTL_BITCOINMINE to the infected machine. The WORM_OTORUN.ASH source code can also be used to exploit a common chain of network vulnerabilities to force systems into Bitcoin pools.
Is the Concept of NFTs Confusing You? Learn Everything There Is To Know
What Happens To Bitcoin-Mining-Infected Systems?
The primary objective of bitcoin-mining malware is to generate Bitcoins for the purposes of cybercriminals. By accessing malicious URLs, BKDR_BTMINE.MNR obtains certain IP addresses. As a result, it uses these IP addresses to transmit and receive information, download other malware, and update its IP database. Additionally, the malware downloads and runs one of three different bitcoin mining programs, as determined by the specifications of the infected system.
The BKDR_BTMINE.DDOS tries to access a number of IP addresses for purposes of sending and receiving data, downloading other malware, obtaining IP addresses, and discovering sites that can be attacked with distributed denial-of-service attacks (DDoS). As soon as it is executed, WORM_KOLAB.SMQX creates a directory containing HKTL_BITCOINMINE, which is Bitcoin-mining Grayware. WORM_KOLAB.SMQX generates Bitcoins with this Grayware in the background. In the course of analyzing the Grayware, it attempted to access a malicious link using a specific username and password but couldn’t.
As part of its attack, WORM_OTORUN.ASH utilizes the Deepbit cryptocurrency mining pool in order to gain access to infected computers. There are bitcoin mining pools that pool the work of multiple Bitcoin miners to process blocks more quickly. Afterward, the participants distribute the Bitcoins generated through the pool.
The Binance NFT Market: A Review
-
Energy footprint
There is a cycle preventing Bitcoin mining from scaling, which is driving its power consumption upward. Bitcoin miners often put more and more computing power into the network in order to mine more coins. In response, the software that runs the network changes a parameter making the mathematical problem of solving a Bitcoin block harder. As a result, miners increase computing power because this problem is harder to solve.
Bitcoin mining energy consumption and its relation to bitcoin mining are as follows:
- Energy consumption by the Bitcoin network is not reduced by more efficient mining gear. As a result, network difficulties will only increase.
- Mining energy consumption of the Bitcoin network increases linearly with lower energy costs
For every proof of work-based currency, the same principle applies. Mining is a peer-to-peer operation that requires Bitcoin network members to collect recent transactions and apply the proof of work scheme to each transaction. This scheme relies on the network periodically recalibrating the current target value T. Obtaining a nonce value enables the miner to:
H(B.N) < T(1)
An example of this would be: B represents the recently performed transactions, N is the random nonce value, and the .’ operator represents concatenation, and H represents Bitcoin hash.
H(S):= SHA256 (SHA256(S))
In order to demonstrate the work, N can be chosen randomly or systematically until equation 1 is satisfied to achieve the proof of work. Upon finding N, the resulting block can be sent to the Bitcoin network and added to the Bitcoin blockchain. Discovering a block earns the finder of that block extra Bitcoins. Bitcoin mining is therefore the act of figuring out the optimal N value.
As a Bitcoin miner, you are limited by the hash rate of your hardware and the cost of running it. As a measure of hash rate, R, the term is often used to refer to Megahashes (Mhash/s). The bit rate, R, is combined with the power consumption, P, in order to compute hardware efficiency, Hardware E = R/P (Mhash/J), a helpful ratio to evaluate various hardware systems.
The mining process began on standard computers. In the period during which Bitcoin gained popularity, mining companies were trying to maximize their hash rates in an arms race. The GPU (Graphics Processing Unit) is ideally suited for Bitcoin mining since it can execute a lot of parallel computations. GPUs became popular among bitcoin miners thanks to standard programming interfaces like OpenCL and CUDA. In addition to having a high hash rate, they also had a very low energy footprint, making them more suitable for mining than usual CPUs. GPU usage increased, so people were forced to find alternatives so they could keep up with the competition. Until Application-Specific Integrated Circuits (ASIC) became popular, Field Programmable Gate Arrays (FPGA) were in vogue. With ASICS, Bitcoin hashes can be performed at higher speeds and with much less energy consumption.
Cloud Mining, What Is It, And Why Are They Preferred?
The cloud mining process taps into cloud computing infrastructure to produce blockchain-based cryptocurrencies. The cloud is fundamental to cloud computing. Generally, a cloud is referred to as a collection of interconnected computers. The computers can be either a personal computer or a network server, both of which can be public or private.
Among other things, Google offers a cloud infrastructure that encompasses both small PCs and high-end servers. In Google’s cloud, users are only allowed access to the device via Google account login.
Cloud computing isn’t confined to a single business or enterprise. A broad set of enterprises and platforms can access the applications and data in the cloud. There is an internet connection for access. This information can be accessed from anywhere, using any computer connected to the Internet (mostly by an authorized user).
Prior to adopting cloud computing for Bitcoin mining, one should realize the value of cloud-based applications. In order to understand why cloud computing is beneficial, it is necessary to consider its advantages. The following are a few highlighted ones:
1: Increase in computer performance
By eliminating the need to store and run a lot of software on the desktop PC, your PC will be more efficient. A cloud network’s computers are faster to start and run because there are fewer processes and programs loaded into memory.
2: Economies of scale in IT infrastructure
Cloud computing can supplement or replace internal computing resources instead of increasing numbers of computers, so as to save an IT company the cost of purchasing more powerful servers. Those organizations with peak traffic demand no longer have to spend money on gear to handle huge amounts of traffic.
3: User-Friendly affordable Computers
Cloud computing’s web-based applications do not require a high-end and cost-exorbitant computer. This PC is not needed for processing power or storage space since the application runs in the cloud, not on the computer.
4: Cost-effective software
The cost of installing software on each computer can be reduced by using cloud-based applications. The application can only be accessed from the cloud by employees using the application. While the desktop software might cost the same in terms of installation and maintenance, IT staff will be able to save money by not having to install and maintain it throughout the organization. Thus, cloud-based technology firms can offer software at much lower prices than firms that maintain on-premises infrastructure.
5: Reduced maintenance issues
In addition to reducing hardware and software maintenance costs, cloud computing significantly reduces organization costs. Maintenance costs are instantly reduced by using fewer servers. Cloud servers are used to run all applications, so there is no need for maintenance on the software front. In addition to providing unlimited storage, cloud technology also provides enhanced data security, speedier computer performance, and instant software upgrades.
Using various cloud-technology services such as these can increase Bitcoin mining efficiency and cost-effectiveness due to the many attractive advantages that cloud services offer.
- Infrastructure as a Service (IaaS)
- Software as a Service (SaaS)
- Platform as a Service (PaaS)
The Implementation Of BTC Cloud Mining
Because Bitcoin’s industry is extremely unpredictable, owning and operating expensive ASICs would be impractical, which calls for a cloud computing solution that would reduce and offset the losses that would occur as a result of the high electricity consumption and maintenance costs.
Cloud mining, as it is known, refers to the process of mining cryptocurrency on a cloud network for cryptocurrencies like Bitcoins.
In other words, miners do not need to own an ASIC in order to conduct mining operations, but they can hire one instead. Mining operations can be stopped when the difficulty in mining networks has increased or when Bitcoin prices fall. Renting these machines provides mining operations a better way to stop mining operations if they experience losses due to falling Bitcoin prices. Infra as a Service is demonstrated here.
For mining, there are several platforms available, such as Amazon EC2 and Digital Ocean, also known as PaaS (Platform as a service). Last but not least, miners can simply rent or lease the hashing power of ASICs from high-end hardware manufacturers that specialize in the development of integrated circuits (ICs).
In more detail, miners can use three types of cloud mining techniques to improve profitability:
-
Hosted mining machines
-
Hosted platform mining
-
Leasing hashing power
Hosted mining machines
In this model, mining equipment is leased or rented to clients who can use it to mine for bitcoins. Bitcoin ASIC mining systems for rent are provided to the clients on a monthly basis; additionally, they may rent a dedicated physical machine for personal use. It is obvious that such a plan would have benefits; such as reducing energy costs resulting from clients running such machines at home as well as reducing carbon emissions.
Hosted platform mining
In order to take advantage of this scheme, a Client has to rent virtual computer resources on which to run their applications.
EC2, Amazon’s cloud computing platform
The Amazon EC2 platform delivers virtual services, also known as Compute Instances, cheaply and quickly via the cloud. Clients must determine the type of instance, selecting one of the template options that come with Windows or Linux, and then deciding how many services (or virtual servers) they need. The entire process can be automated by using the AWS management console or by an API using an SDK in any programming language.
When the API code is implemented, client instances will start running, with full administrative and access rights just like any other server. With EC2, you can choose from a range of instance types tailored to different scenarios.
Among the options are small and economical instances for low-volume applications, as well as specialized clustered computers for supercomputer-based workloads on-demand and cloud-based computing. With Amazon EC2, you will have instances optimized for computing, memory, and storage, as well as high-performance ASICs.
By doing so, clients can choose the right price and performance combination for the workload they are running. Furthermore, resizing the instance is easy, depending on the client’s requirements. It is possible to adjust the instance to maximize the performance at times when the hashing rates and difficulty of the network are high. Payment is based on the complexity of instances
Leasing hashing power
In the scheme, mining companies rent out ASICs that can have an extremely high hash rate to miners. Miner’s choice of plan determines the hashing rate. It is important to select a plan that is profitable. Here are a few of the service providers:
Cloud Hashing: Under this service, clients are awarded a one-year contract specifying the amount of hashing power they require. An average contract can range from 30Gh/s to 350Gh/s.
Hash Rack: clients pay for an indefinite period of time (i.e. up to the point the hardware breaks), and a part of that amount is reinvested to increase power. As an added feature, users can move “hashpacks” between several rigs they own.
Bit Miner: This application offers collective mining using a rent-sharing model. As an example, an Ant Miner rig (6×180 GHEPS) consists of 10,000 shares, each priced at $5.50. Renting these rigs is so competitively priced
Bit of Glory: The company offers 12-month contracts for 100GH/sec, 500GH/sec, and 1TH/sec.
Cex.io: The Cex.io platform allows users to mine and trade hashing speeds (GH/s). Profits are distributed using PPLNS (pay per last N shares) and all hash rates are guaranteed.
E-pickaxe: Payments for e-pickaxe contracts are made using Bitcoins. Contracts can last for one year to indefinitely. It is worth noting, however, that the amount of GH per contract is not fixed because, as they put it, “as we invest in more hardware, your contract will also gain access to it”, that is, all the benefits of new hardware throughout the contract period are yours.
FINAL ANALYSIS
Over the years, mining techniques have evolved at a staggering rate to maximize hashing rates (and therefore profits). The mining machine industry is undergoing rapid technological changes at an unprecedented rate, making stability a question. Since Bitcoins were introduced in 2009, miners have moved from using CPUs to dedicated ASIC machines. As a result, any long-term investment in cryptocurrencies cannot be considered without significant risks due to fluctuating values.
Due to the complexity of the hash generated and the increasing number of people mining bitcoins, the amount of computation required for transaction validation has been increasing exponentially. Cloud mining by leasing machines seems to be the best course of action, given the perilous nature of mining with private ASICs and similar machines, where profitability is stacked against them. This offers greater chances of profit and easier exit options with a low initial investment.
However, even many cloud mining providers find that the initial cost of buying large and powerful mining machines, including security features, air conditioning, and electricity to run the systems is exceedingly high, as demonstrated by the temporary suspension of key operators like CEX.IO. Considering government regulations and the general attitude toward cryptocurrencies, it is inevitable that Bitcoin values will rise and fall in unexpected ways time and time again, so miners need to be prepared. Even in such a case, Bitcoin price will rise proportionally to a rise in hashing difficulty, despite such sudden drops in price.
