
Security, What is it
Generally speaking, personal security, is the state of being free from danger, and this is the center of the concept of security. When we talk about the security of things around us we need to analyze them from this very perspective, because ultimately this is what really matters. How does the item, or the lack of it, affect us physically. Let us take an example.
For a diabetic person, insulin supplement is an important asset. The lack of it can cause harm to the person, so when we talk about securing this asset, we refer mostly to the fact that it needs to be available to this person when needed. This means preventing it from being stolen, protecting it from degradation, and so on. If we talk about an insulin pump, things are a little bit different. This is a more complex device that is used to automatically verify the glycemia and automatically inject the appropriate amount of insulin. Through the nature of its interaction with the body, this device has the potential do harm to the person, if somebody else had access to its configuration. So from the perspective of personal security, it is not enough if we prevented the theft of the device, we have to make sure nobody has access to it, while in use. We can see how the method of ensuring security is different for different things when we look at it from the unique perspective of the personal security of the individual who is being affected by the “thing”. The same principle applies when the beneficiary of the item is not one individual but rather a group of individuals, we will have to analyze the security of the device from the perspective of personal security of the group. The result is similar only a little bit more complex. In this instance it is not enough if all the security of each individual of the group is ensured, we also have to make sure that the group as an entity, as a whole, is not harmed. For instance if the device leaves individuals unaffected but disrupts the functioning of the group, this cannot be considered secured from the perspective of the group. To see a concrete example, such a group can be a company, and the disruption of the group could mean bankruptcy for the company. But even if it does not end up complete disruption of the group, in principle any damage incurred by a group which hinders its normal operation has to be considered a breach of security: this may be loss of money, loss of reputation, temporary dysfunction, anything.
Security in Cyberspace
There is an enormous amount of talk about cybersecruity and this is for good reason because cybersecurity, the security of things in cyberspace is no longer a marginal aspect of our lives. The root principle of cybersecurity is no different than that of any other security, only it adds a secondary perspective to the concept, meaning that rather than looking at security from a general perspective, solely through the perspective of personal security of the affected entity, we look at an even more filtered subset of this, which has to do with the cyberworld. So when we talk about cybersecurity we no longer take into consideration all those cases of personal security that can affect us directly, physically, such as having a car accident and being hurt, or being attacked on the street by a criminal, or not being able to secure food and shelter for the family. Because of this, there is a little bit of disconnect in the sense that cybersecurity gets a somewhat lesser attention, not being perceived as being so imminent. Cyberdangers are not considered as being clear and present dangers, like those that are violent in nature. To put it in perspective, cyberterrorism, while it’s talked about, does not create nearly as big a social unrest as does terrorism in the real world. Discussions are mostly limited to expert groups and the general public is largely ignorant to the subject. This, however is a dangerous phenomenon, because cyberterrorism has the potential to inflict just as big a damage, both to groups and individuals, only in an indirect manner. The reason for this, is that our real, physical, life is extremely connected to the cyberspace, in fact we could even say it is inseparably connected, to the degree that it would cause physical harm if separated.
Like with electricity, this is hard to perceive, until it actually happens. We simply take these things for granted, but when in winter time, with freezing temperatures outside, a city is left without electricity due to a solar storm or some violent weather, the consequences can be severe: there is no light, central heating systems don’t work, because they need electricity even if their main fuel is gas, water distribution halts because pumping stations need electricity, hospitals, traffic, and so on, nothing works any more. And while there was a period when society functioned just well without electricity, that is not the case any more. The same is true for our information infrastructure. We don’t care very much if the banking system is down, it seems so far away from hurting us physically, except when we need to use our credit card to buy bread. Or, if we need to pay the toll on the bridge and we can’t, which causes massive traffic jams, which prevents people from getting to work and ambulances to get to where they are needed and an entire cascade effect starts that has the potential not only to disrupt society on massive scale, but it could even cost lives. It is difficult to notice, the presence of information technology when it is there, just like we don’t consciously notice electricity every time we flick a switch to turn on the light or the microwave oven, but nowadays almost every device has some information technology inside: planes, trains, cars, ship yards, washing machines, and so on. Many of those are embedded systems so the only security concern is to make sure it works, be available when needed. These kind of information technology infused device are confined to a space, like a house or some other premises, so by protecting this space we can make sure perpetrators cannot steal them or use them against us. These information technology devices follow a consolidated environment model, in which they are protected by a secure enclosure and therefore they become secure themselves.
Security in a consolidated environment
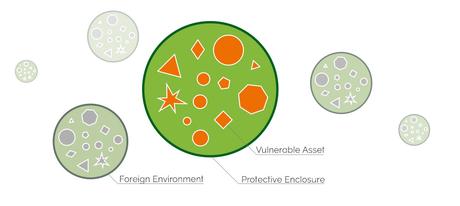
This consolidated environment is the most entrenched view of security and there are many examples of such infrastructures in our lives, starting from fortresses, medieval castles, to modern military bases, secured research facilities, company buildings, including small ones and of course, our homes. This model is also relatively safe and easy to implement: as long as one makes sure the perimeter is protected, everything that is inside, no matter how insecure by nature, will be secured by placement. To secure such environment, we need a reasonably impenetrable perimeter, like walls and an entrance where we can place all sorts of security checks to see what comes in and goes out. Such security checks are plentiful and highly efficient, we have great locking systems, alarm systems, biometric screening solutions and so on. These aren’t necessarily complex technological devices, they are often cheap and available to everybody. Biometry for instance is not a new thing, a security guard or even a secretary is extremely good at facial recognition so they can easily spot strangers should they try to enter the building. A dog is an excellent biometric filter and it is not at all too complicated or expensive to implement one in the house. So while we don’t think of these as security tools in so many words, we do know intrinsically how to use them to secure a consolidated, closed, environment.
Securing a consolidated IT infrastructure is very similar: we take all of our computers and electronic devices and place them inside a secured environment. From an electronic access perspective we raise a firewall between this infrastructure and the cyberspace at large. It is important to reiterate that in order to secure this IT infrastructure we actually need to secure two perimeters, not just one: one is the physical perimeter, and the other is the electronic perimeter. When we talk about cybersecurity in the context of this consolidated environment, we mean securing the electronic perimeter. The reason why we focus on the electronic access alone is because this one is considerably harder to secure and we consider the physical one, intrinsically secure by comparison. This difficulty in securing the electronic perimeter is due partly to the complexity and partly to the inherent handicaps that this world presents: in cyberspace those that enter the perimeter don’t have a face, so we must make use of other, less reliable identification mechanisms, like password. Imagine a company where everybody wore a mask, employees and visitors alike. How would you be able to tell who you can trust and who is an intruder?
Security in a distributed environment
The distributed environment is radically different from the consolidated environment and not well understood by people at large. Even if people do understand that in a distributed environment things are not confined to one security perimeter, but rather dispersed over multiple such perimeters, people tend to fall back and understand the model through the perspective of the consolidated environment: it is not one secure environment, it is many secure environments, so it should be OK. It is not. When it comes to security, this environment has an inverse synergy in which the whole is less than the sum of the components. In fact the security of the whole is considerably less than the security of each of the components individually, but in order to better understand this distributed system, let us take an example from real life first and then work our way into the cyberworld.
A good example of such distributed system, that is actually in places for a very long time, is the banking system. We do not keep all our valuables at home, we take some of them to a bank and place them into an account or safety deposit box. Now we have our home, one secure perimeter and the bank the other secure perimeter and the totality of our assets spans across both: we have some artifacts at home, money in a bank account, jewelry in a safety deposit box and so on. Most people will argue that this is actually better than the model when all the assets were in one’s house, because the security of the bank is a lot better than that of a house. For the period of time while the asset sits in the safety deposit box, inside the bank’s vault, this would indeed be true, but this does not accurately reflect the entire usage cycle of the asset. If we consider the period of vulnerability while the item is in transit we will start chipping away at this security. If this is an asset that we use on a daily bases and in the morning it needs to be transferred to the office and in the afternoon back into the vault, this unsafe transitory state, where the asset is neither in the bank’s vault nor in the secure perimeter of the office, is becoming a security hazard. If the bank gets bored of taking us into the vault twice every day and sticks the safety deposit boxes door out through the window, so that we can access the asset at will, the entire aura of security that surrounds the bank becomes nothing but smoke. After all, at this stage, all that separates a stranger from the asset in the box, within this service oriented architecture (SOA), is the key to the box. It does not matter how secure the bank is, the box does not benefit from this security because it is not entirely in the bank any more. Its access point sticks out from the secure perimeter and into the wild.
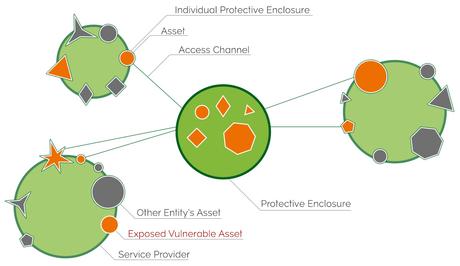
If this paradoxical scenario sounds familiar it’s because we face it on a daily basis, every time we access our informational assets within the cyberspace. Our mailbox, internet banking account, backup space, CRM, ERP and all those services out there in the cloud may be on the secure servers of the service provider, but their doors stick out through the allegorical window so that we can access it 24/7 and the only thing that separates a cybercriminal from the stuff we have in those spaces, is an authentication process, which often consist of nothing more than a password.
We can see now that the security picture portraying multiple consolidated environments is not applicable any more. It is erroneous and extremely dangerous to consider our asset safe only because it is in the custody of a third party whose security perimeter is better than that of our home’s. In fact, all that matters is the security of the space we hire at this service provider. So the real question to any such service provider is not “how secure is your environment?”, that is only partially relevant, but rather “how do you make sure the space I rent is secure”, which translates to subsequent questions like: “is the wall of my space strong enough?”, “can my information be stolen while in transit?”, “how do they make sure nobody can enter my space but me?”. There is of course a flip side to this relation. My asset being in the custody of some service provider, it would seem it is solely their responsibility to protecting it (asset in the vault model), but by giving me direct, uncontrolled, 24/7 access to my asset, the service provider introduces a great liability, me. I can create a weak key, I can share the key with somebody else, I can leave it unprotected so that somebody can copy it or I can leave clues around which would allow somebody to reverse engineer my key and impersonate me. So to complement the model I will also add the questions: “do I understand that I am responsible for the key to my locker”, “have I made sure this key cannot be stolen or reproduced”. The SoA model is a very sensitive and complicated security model which can fail through so many means. Responsibility is shared among the service provider and the client and if we don’t understand where the weaknesses are or if we form a misconceived sense of security, we risk not having security at all. Security is not cumulative in this distributed environment, but rather less than the weakest security element, so in a setup where our security has multiple dependencies, the tear will happen at the weakest point. When a climber is on the cliff, his life depends on multiple factors: the strength of the rope, the strength of the carabiner, that of the rock, the anchor, it depends on how well he tied his knots, on the person who seconds him, etc. Should any of these elements fail, the entire security setup failed.

This takes us back to the definition of security which boils down to personal security, us being safe from danger and to the fact that security lost, ultimately means subjecting our very selves, our business or our loved ones to the risk of being harmed. So in a distributed environment there cannot be such a thing as “Vulnerable Asset”, because there are no such things as secure perimeters. The assets themselves need to be secure by nature, or have around them little individual secure perimeters.
Security in the IoT space
So far, the discussion on distributed security observed mostly the availability aspect of assets, in the sense that we looked at security as the concept of protecting the asset from being taken away from us. There are many such assets that are important to us as static resources, money and information are clear representatives of this class, within the context of our discussion. But in the beginning I pointed out a secondary aspect of security, one that involves the class of dynamic resources, the kind we need to make sure are not accessed by malicious entities because they can cause harm through the nature of their scope. Within the context of cybersecurity, this takes us into the world of the Internet Of Things, a web of information technology oriented devices meant to perform jobs in order to make our lives better.
From the perspective of need for security to these class of devices, the applied principles are somewhat similar to the static ones, but they are more complex and they have to be stricter and better, because these devices are more dangerous. IoT devices are always-on devices, they feed out information and they may receive information at all times. These devices are also a lot more self contained, in the sense that although they follow the distributed model, they follow a more complex service oriented model. Services like internet banking, they have their front end sticking out into the public space, but their back end is with the service provider and because the service provider is responsible for keeping it safe, they invest a great deal of effort into making them as secure as possible, given the inherent insecure nature of the model.
By their nature, IoT devices are usually in the user’s custody and therefore they stick out their front end from the user’s perimeter, which is, as we noted earlier, more often than not, less secure than that of a service provider. Sometimes, the other part of the IoT, the collected data, is transmitted back to the service provider and hosted on their premises, thus making this a more complex service oriented architecture: not only the client has assets at the service provider, but now the service provider has assets within the client’s perimeter too. However, there is a great deal less incentive on the account of the manufacturer to secure these devices because the pressure of keeping them secure is not that great. Sometimes the data does not go back to a service provider at all, sometimes the device is not manufactured by the service provider so there is a lot of gray area when it comes to the responsibility of implementing security. This represents a lack of understanding in the security model of the Internet of Things and of course a disaster in making because several factors destructively interact in such ways that we end up with no security at all instead of the much needed, better, stricter security: devices are more complex so harder to secure, the manufacturer invests less in securing them because they don’t impose the same level of liability, they are being used on the premises of the client who often has no experience with security and has no clue that they just placed a Trojan in their house. It is a fundamental misconception to think that an IoT device, such a Smart TV is secure because it is in our house and it is guarded by our dog. The entrance to the IoT device is not through the front door, is through the internet. So instead of securing the device by bringing it into our secure perimeter we are in fact breaking the security of our perimeter by allowing information to leak out, information that can be used to penetrate the secure perimeter that we have built for us.
So just like in the case of the service oriented architecture, we have to find out which are the dependency points (the rope, the rock, the carabiner) of the system, and make sure there is sufficient security at each of these points, because they each represent a potential weakness, through which the security of the entire system fails and harm can be caused to the entity using it. It would be nice if we could formulate some questions for the IoT model too, that helped us understand what these dependency points are. Unfortunately it is not that easy, because responsibility is thinned out, more convoluted, and as of yet, no standard exists to which IoT devices should adhere to guarantee security at each dependency point. I will nevertheless attempt to formulate these questions and at least try to identify these points even if naming the owner of the dependency remains impossible at this time. It is after all, ultimately our responsibility to makes sure these questions are answered and if we are unable to answer even one of them, to refrain ourselves from placing such a device into our service, because we never know who it will be really servicing. In a sens, the Internet of Things will be to the society, similar with what an insulin pump is to a diabetic: it has the potential to considerably improve our quality of life, but at the same time it represents a risk to personal security if we, the beneficiaries, cannot provide adequate protection from malicious use. This is by no means an exhaustive list of questions and they should be treated as a minimum requirement when it comes to IoT infrastructure security:
- what kind of information the device collects
- where does the information from the device go
- can the information collected by the device be intercepted while in transit
- can the information collected by the device be stolen while in storage
- who owns the information that is collected by the device
- who controls the device
- how is the device updated if a weakness is found in the system
- how do I know if the device is under the control of a malicious entity
- how do I shut down and clean the device if it has gotten under the control of a malicious entity
- in what way am I or those I am responsible for, going to be harmed if any of these dependency points failed
This last question is really important. This is the question based on which we can decide to make compromises should we be unable to answer all of the previous questions. The Internet of Things is as of yet an unborn baby and many things will change by the time it will have materialized. It is everybody’s responsibility to find as many as possible questions that pertain to each particular case of IoT deployment they conduct and to make sure they are answered.
Last words
Security is a complex concept by itself and as we’ve seen the more complicated the environment, the more complex it becomes. So while it is hard to find a general formula for security, it in not that hard to understand security for a particular case, find out what are the dependency points and what are the questions that need to be asked to ensure security is covered for all these points. All it takes is common sens, a little intellectual exercise and an open mind. Just consider all services, all assets, paths of the assets, parties that interact with the assets, the importance of the assets, how the assets and services interact and all those aspects that might affect you or your business with respect to a particular asset / service and take them through a rigorous process of questioning. Then create a process through which you minimize the likelihood of incurring damage. After that, take insurance measures and ultimately run all this through a professional. While a specialist can do all these for you by himself, I still recommend you do this exercise, because it will help you better understand your infrastructure and you will be less likely to make mistakes. It’s considerable effort but it is well worth it, and even if you can’t afford a specialist to sign off on your plan, you will be better of than assuming security exists by default. It does not.

