The Intercept_'s Micah Lee had a very interesting interview with NSA Whistleblower Edward Snowden who is right now granted an extended three-year temporary asylum by Russia. His guide to privacy is more than just staying anonymous online.
With the leaks we now know, you and me are probably being watched by the government. our digital life which we always felt in control of might actually have been an open art exhibition for governments to gaze at. There is not much we can do to fix the damage but a lot can be done to be cautious in future and get back some control of our own privacy by following a very simple guide to privacy. After all your privacy has to in your control and not out of control. Information on you should be limited to as much as you want to give.

Snowden as I like to refer him as a privacy savant, gave a lot of information on what one can do to secure their privacy in his interview it can be considered a simple guide to privacy. This interview serves as a guide to protecting your privacy and protecting yourself from the possible government mass surveillance.
Make no mistake, this guide to privacy isn't something only someone with sensitive information or documents should be following. Rather this guide is for any concerned citizen, any citizen who feels responsible for their privacy.
It's not about something to hide, it's about something to lose.
- Edward Snowden (@Snowden) November 4, 2015
EDWARD SNOWDEN'S GUIDE TO PRIVACY
USE SECURE APPS
Encrypt your phone calls and text messages. You can do that by using a Free app Signal by Open Whisper systems. This app encrypts communications so if it's intercepted by any person or agency it can't be read or be listened to. Everything from calling to sending a quick message done in this app is end-to-end encrypted and secure.
Something that people forget about cellphones in general, of any type, is that you're leaving a permanent record of all of your physical locations as you move around. ... The problem with cellphones is they're basically always talking about you, even when you're not using them.
ENCRYPT HARD DRIVE
If your computer is stolen, no personal data would ever be revealed. The data could include your pictures, your home address, your work information, your family details which if unencrypted could be openly shared online or make your vulnerable.
INSTALL HTTPS EVERYWHERE
Install HTTPS Everywhere by EFF in your browser. This is an extension for all your browser and is made by Electronic Frontier Foundation(EFF) with the only aim to make sure you browser websites securely. This security add-on/extension will force all browser communication with the website to be encrypted.
USE TOR
Use Tor while browsing sensitive information .This can be achieved by using a Tor browser or Tor client. Tor browser is much easier to install and use. Both give the same result and keep you anonymous. Once connected to the Tor network your browsing history cannot be traced back to you. By the time you reach the website it has passed throw various nodes and it becomes nearly impossible to track your visit to the website.
TAKE SECURITY SERIOUSLY
Take your security seriously. Our friends and family know us well and now so does Facebook and Twitter. Social media has made our life an open book. Things like grandma's middle name, first pet's name or your mother's maiden name are known. This means most security question answers on the forgot password option of most accounts could be known to someone. So always know what information you are putting out there and what information has to be kept secret.
USE PASSWORD MANAGER
A password manager can be a lot more than being your password saving vault. You can use it to generate unique passwords which are unbreakable. Using password managers which sync with cloud should be avoided as your passwords (even if kept encrypted) on cloud is still a threat. There are many open source password managers which are reputed and very secure. KeePassX is one of the most abundantly used password manager by people who care about their security and privacy. KeePassX is free, open source, cross-platform, and never stores anything in the cloud.
USE TWO FACTOR AUTHENTICATION
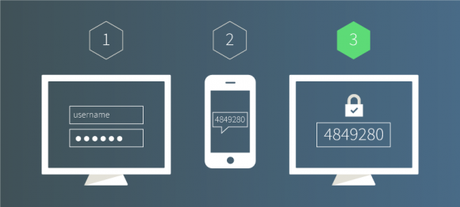
Enabling this will make sure that even if your password is leaked or shared, your account cannot be accessed by anyone but you. In two-factor authentication the first factor is your password which once entered prompts you to put another code which you get a code on your phone/physical device. This device becomes the second factor in two factor authentication. Gmail, Facebook, Twitter, Yahoo!, battle.net, Dropbox, Github, iCloud, Evernote and even some banks are working on enabling it. Full list of websites, services and institutions using it can be found here.
USE AD-BLOCKER
Install an ad-blocker for your browser. Don't misunderstand, this doesn't mean websites are bad or serving bad ads. Snowden is emphasizing on using an ad-blocker to save yourself from your own service providers who serve their own ads in plaintext http connections. He says "As long as service providers are serving ads with active content that require the use of Javascript to display, that have some kind of active content like Flash embedded in it, anything that can be a vector for attack in your web browser - you should be actively trying to block these. Because if the service provider is not working to protect the sanctity of the relationship between reader and publisher, you have not just a right but a duty to take every effort to protect yourself in response."
To read the complete interview, please head over to The Intercept for a really interesting talk about privacy and personal web security. Edward Snowden is just not a NSA whistleblower but a very smart, intelligent and honest person who leaves nothing at door when he talks about this topic, a topic which has changed his life from a computer professional to a privacy activist & a wanted criminal.
If you liked reading this, do read our guide to How to Stay Anonymous Online