
There’s a very nasty computer virus called CryptoLocker that targets computers running Microsoft Windows.
First surfacing in September 2013, the virus may be disguised as a legitimate email attachment. When you open the attachment, however, unlike other viruses that simply delete your files, thereby allowing for the possibility of some file recovery, CryptoLocker will securely encrypt them using a special private key.
When your computer’s been infected by CryptoLocker, you’ll see a message like this:
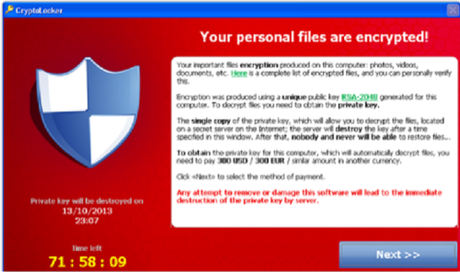
Recovery of your files is impossible without CryptoLocker’s encryption key that they’ll give you only in exchange for a ransom payment.
That is why CryptoLocker is called a ransom malware.
The ransom must be paid by a stated deadline through either Bitcoin or a pre-paid voucher.
Although the CryptoLocker virus itself is readily removed, the files in your computer remain encrypted until you pay the ransom. Many say that the ransom should not be paid, but do not offer any way to recover files. To make things worse, paying the ransom is no guarantee that your files will be decrypted and restored to you. Other malware has employed similar tactics in the past, but CryptoLocker’s encryption is much more secure and is currently not possible to crack.
The steps to guard against CryptoLocker are the same good practices that should be employed to guard against any malware attack or hardware failure:
1. Make sure you’re using antivirus software and that it’s kept up to date. Thankfully, most antivirus applications can now detect and remove CryptoLocker, but are only of use if they catch it before the encryption occurs.
2. Make sure that you regularly back up all your data. These backups should be in a form that’s disconnected from your computer by using an external USB drive that you don’t keep permanently connected to your computer. CryptoLocker will seek out any connected USB drives and network shares, and attempt to encrypt those files, too. This can also apply to files being synced to Cloud services, although you should often be able to retrieve previous, and therefore unencrypted, versions of these files via the Cloud service provider. Users of Windows starting with XP Service Pack 2 may also be able to retrieve previous (and therefore unencrypted) versions of their files, by right-clicking on an encrypted file and selecting “Properties,” then “Previous Versions.”
3. Email is CryptoLocker’s primary mode of attack, so avoid opening any email attachments from untrusted sources or that appear in any way suspicious. This should include attachments sent from banks or financial institutions and, particularly in the case of CryptoLocker, from courier companies or from Companies House.
4. Make sure the email scanning feature of your antivirus software is configured and enabled.
PCAdvisor suggests that you check right now whether CryptoLocker has found its way onto your PC by downloading and run Malwarebytes Anti-Malware. This will scan for the Trojan and remove it for you if discovered.
I have Malwarebytes Anti-Malware, one of three antivirus software I use. Malwarebytes is free. In fact, it’s running a quick scan on my laptop right now.
See also:
- How to avoid the best malware scams
- What’s the best antivirus?
Sources: PCAdvisor, Wikipedia
H/t FOTM’s joandarc
~Eowyn

