As scary as it sounds, if Google is ordered by a court Google can remotely bypass passcode of older version of Android. The court can give such an order to help investigators easily view the contents of a particular device if needed in their investigation.

"Forensic examiners are able to bypass passcodes on some of those devices using a variety of forensic techniques.
For some other types of Android devices, Google can reset the passcodes when served with a search warrant and an order instructing them to assist law enforcement to extract data from the device. This process can be done by Google remotely and allows forensic examiners to view the contents of a device."
As per The New York District Attorney's Office, devices which have full disk encryption cannot be bypassed. This means devices running Android 5.0 or higher are safe.
Only about 25% of the total devices being used are using Android 5.0 (Lollipop) and Android 6.0 (Marshmallow), the rest 74% are using Froyo, Gingerbread, Ice Cream Sandwich, Jelly Bean & KitKat.
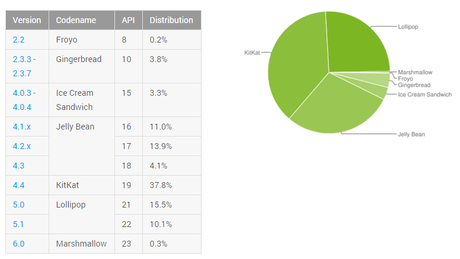
This userbase of 74% using devices running Android 2.2 to Android 4.4 are at risk of being snooped in by investigators under the name of justice. But that isn't it. In case of Android, full disk encryption isn't implemented by default. So users who haven't enabled this security feature are still at the risk of being vulnerable to this android passcode bypass vulnerability.
For Android devices running operating systems Lollipop 5.0 and above, however, Google plans to use default full-disk encryption, like that being used by Apple, that will make it impossible for Google to comply with search warrants and orders instructing them to assist with device data extraction. Full-disk encryption has not yet been implemented as a default on all Android devices running Lollipop 5.0 and later systems, but has been implemented on certain Nexus (Google-controlled) devices. Generally, users have the option to enable full-disk encryption on their current Android devices, whether or not the device is running Lollipop 5.0, but doing so causes certain inconveniences, risks, and performance issues, which are likely to exist until OEMs are required to standardize certain features.
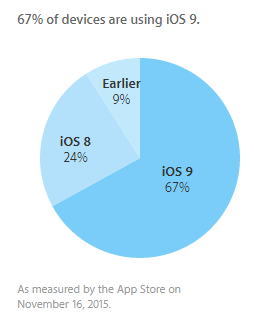
On the contrary, Apple's devices are pretty safe. Any device running iOS8 and above cannot be bypassed remotely by Apple as full encryption is enabled by default . The iOS9 adoption rate has been significant. Only 9% iOS users are using earlier version of vulnerable iOS version. This means 91% of iOS users are secured and are using fully encrypted devices.
