It is widely believed in the SEO community, that 2014 will be the year of negative SEO – a strategy based on downgrading a website’s search result rankings through a wide range of methods. Here’s a comprehensive guide on how to avoid becoming a negative seo victim and protect your website from various attempts to sabotage its position.
Malware and hacks
If someone is set to sabotage your page’s ranking results in search engines, the first thing he would probably try is to attack the website directly. Even though your website looks perfectly fine once you load it, search engines might be seeing here something entirely different. To make sure you’re not a victim of such a tactic, follow these simple steps:
TIP 1) Make sure your CMS and plug-ins are updated
That’s an absolute must to ensure your website works fine. There are plenty of hacked pages to be found on Joomla, WordPress or Drupal, so beware and always make sure that your CMS and plug-ins are up to date.
TIP 2) Compare your website to the one available through Google Cache
Now, you might think your website looks like this:

While Google actually sees it like this (click to enlarge):

You can check the Google version of your website easily, just type in Google cache:YourWebsite.com and you’ll instantly see the page exactly as it’s seen by Google. If what you see differs from what you were supposed to see, this might be a harbinger of search engine performance problems.
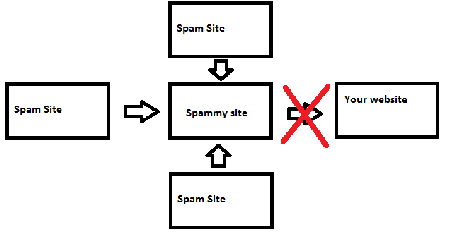
Link Based Attacks
Link based attacks attacks are definitely the easiest and most popular ones to pull off. In this case, you should look out for things like xrumer blasts, or a gigantic surge of comments, link networks, guest books, forum profiles, anchor rich links and many more.

The key to success here is constant vigilance – you might want to check the new links to your website more often than not. It’s best to use three sources of information at the same time:
- Google Webmaster Tools – for the new links
- Majestic SEO – by adding yourself at Majestic you can easily monitor all the links to your website for free
- Keep an eye on the server logs
If you spot low quality links, here are some basic steps to follow. Once you discover a massive surge of links that you suspect might constitute an attack, you need to immediately renounce them. The utility to use in this case is a disavow tool, and you can find a detailed instruction on how to use it correctly here.
Considering all that, the next necessary tip is the following:
TIP 3) Check regularly the Google Webmaster Tools, Majestic SEO and Server logs (at least weekly)
Unfortunately, more drastic measures that might pose a threat to your website existence. Among those, you find the so called redirect attacks, which most commonly are based on redirecting to 301, 302, IP based redirections and rel=canonical.
All redirections should be visible at Google Webmaster Tools or opensiteexplorer.org. If you notice this kind of attack, you simply need to block it. Here’s a selection of the best methods in doing so:
- Checking the redirection host IP (e.g. ping.eu) and blocking this IP in .htaccess
- Order Allow,Deny
Allow from all
Deny from “first spammer’s IP”
Deny from “second spammer’s IP”
- Blocking host IPs through a firewall
- Adding the redirecting domain to disavow (this works exclusively for Google)
TIP 4) Beware of attacks through redirect
You must remember that these kinds of attacks are not always the work of your competitors. I once had a client trying to enhance the rank of his medical practice by using a link network. Luckily monitoring the activity through Google Webmaster Tools let me notice the problem quickly and I used noindex on the site in order to block it for Google. A different but equally effective thing to do would be redirecting the website to another address supplied with a 404 error page.
Backlink removal
There are tools for creating fake e-mails that look as if they were sent form a certain domain. This leaves an opportunity for spammers to use the domain. Here, your competition might analyze the backlinks, use a site like the one mentioned above to send a request to remove the links to the domain owners. It’s therefore advised to always check whether the links are active, and here a tool called scrapebox comes in handy. The Page Scanner plug-in will instantly check the status of the list of links imported from Majestic SEO or Google Webmaster Tools. You can find more about this step in here. If the links are not there, don’t hesitate and check with the website owner.
TIP 5) Check if your links are not being removed
Fake reviews
A method of obtaining fake reviews is through fiverrr or having them actually written by someone. This is something I’m still figuring out a way of dealing with, so if you’ve got a foolproof method, let me know in the comments.
TIP 6) Beware of fake reviews
User Generated Content
Examine the content created by the users on your website (UGC). Obviously, it’s impossible to check every single thing someone wrote on a blog or forum, so this is where filters come in. Properly configured, filters should take care of keywords that might result in blocking the account adsense. Beware of parental filters as well, as they can radically diminish the popularity of your website.
TIP 7) Monitor your content for adsense forbidden keywords
You can easily check it in the keyword list and site: parameter at scrapebox
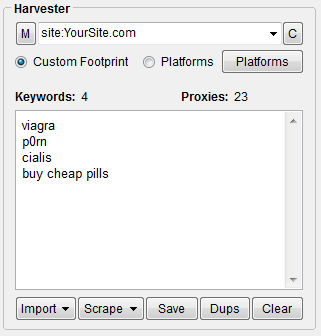
If you find sites that contain these keywords, it’s best to simply remove them.
Don’t index the search sites. If someone types in an obscene word (search.php?search=Family_Unfriendly_Keyword) you might:
- Be banned in AdSense
- Have your website grow to be less popular as it becomes dangerous
TIP 8) Always check what you index in search engines and what you transfer in your protocols
Apart from preventing indexing, you can also utilize the Get method to stop any data transfer. Similarly, it’s not worth it to transfer information using CGI scripts.http://www.htmlcodetutorial.com/cgi-bin/mycgi.pl?town=very+bad+word
If someone links to these sites, the whole portal might become affected.
How to avoid this? Simply by transferring through POST. In this case the site won’t be available for indexing, neither by Google, nor by other web crawlers.
Duplicate Content
Check if your website does not include duplicate content. Your competitors will be more than happy to link to the site, as long as you don’t have redirects or canonicals.
If your main site is www.example.com, make sure that you don’t index:
1) Other subdomains like wwww.example.com
2) Variants lacking www like http://example.com
3) Same content, but visible after typing for example index.html like www.example.com/index.htm
4) Same content that pops up after sorting: www.example.com/?sort=something
This probably won’t cause you to drop to the bottom of Google results instantly, but since Google doesn’t like it – it eventually will happen if you don’t act on it.
TIP 9) Check your canonicals and redirects
Site Speed
Attacks that regard target site speed are usually based on a so called Denial of Service . It might slow down or completely shut down the service, denying Google access to the website or radically reducing the server speed. You can find more on this here
Other options for defence against this kind of attack can be found here and here.
TIP 10) Beware of DDOS attacks
Content Theft
Content theft happens. Some webmasters of strong domains employ this tactic, hoping that by being initially higher than you in search rankings, they’ll get your content (the original) to look like a duplicate. Consider doing this:
1. Don’t add all the post content in RSS, but only a part of it – for wordpress use yoast SEO plugin
2. Set rel=canonical on your domain – even if they steal for you, they will still refer to you as the author.
3. Set rel=author as you
If that doesn’t work, try using the DMCA Request
TIP 11) Protect yourself against content theft
Advanced Attack Methods
If you connect to your server through SSH, you can monitor the activity on high ports owned by the user of the www server. They might be used to control your server through www.
TIP 12) [Advanced] Monitor SSH Access
DNS Attacks
Your website might fall victim to a DNS attack, which will result in displaying a different website. This doesn’t happen often, but it’s best to be aware of this possibility. Check more here.
Conclusion
There are multiple ways of harming your websites search engine rankings. Luckily most of them can be countered, as long as you’re aware of the threats and you’re prepared for them. Of course it is virtually impossible to make your website completely resistant to all forms of attacks, but if you prepare well enough you can minimize the risks significantly. Let’s once again go through what can be done about it:
Daily:
Do daily backup
Weekly:
Make sure your CMS and plug-ins are updated
Compare your website to the one available through Google Cache
Check regularly the Google Webmaster Tools, Majestic SEO and Server logs (at least weekly)
Beware of attacks through redirect
Check if your links are not being removed
Monitor your content for adsense forbidden keywords
Always check what you index in search engines and what you transfer in your protocols
Monthly:
Check SSH ports open
Find fake reviews
Check your canonicals and redirects
Prepare for DDOS attacks
