 Highly skillful and sophisticated state-sponsored hackers are tracking the personal military soldier’s Android phone gadgets to spy on the activities and to get access to the data. According to the research of Lookout & Kaspersky stated that almost 100 soldiers of Military have been attacked with the malware. Reports also stated that “Dubbed ViperRat” is the malware that has been used to spy on soldiers private android devices and it further steals the data such as photos and audios recording, through the targeted smartphones.
Highly skillful and sophisticated state-sponsored hackers are tracking the personal military soldier’s Android phone gadgets to spy on the activities and to get access to the data. According to the research of Lookout & Kaspersky stated that almost 100 soldiers of Military have been attacked with the malware. Reports also stated that “Dubbed ViperRat” is the malware that has been used to spy on soldiers private android devices and it further steals the data such as photos and audios recording, through the targeted smartphones.
Military soldiers have been attacked by the state-sponsored highly skillful hackers and they have got access to their personal android phones. The hackers have used a malware named “Dubbed ViperRat” and they have penetrated into the soldier’s phone and steal the data of the type that is valuable. The malware has steeled the photos and recording of the audio conversations of almost 100 military personnel, according to the research of lookout and Kaspersky further added that.
According to the Modus Operandi Security Firm
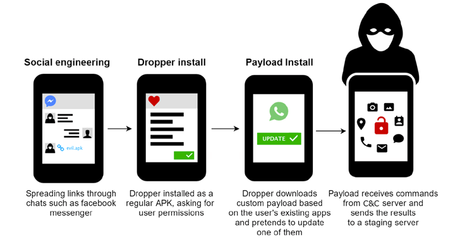
The security organization stated that, The Defense Forces personal android phones have been compromised through the social engineering methods –the military personnel were attacked via Facebook messenger and as well as through social networks in order to get ingress into the communications with hackers that pretends to be as attractive women of many countries such as Canada, Germany, and Switzerland.
The soldiers were getting into the trap by installing a trojanized version of multiple and particularly permissible android chat apps, SR Chat and YeeCall Pro, for effective and user-friendly communication.
The malicious malware has been used and prevailed with the help of dropper hidden in the Android phones apps such as Billiards game, in favorite songs, and further move up into the iOS app, that usually citizens are used to of and that is easily available into the Google Play Store.
Then the app gets started to get ingress into the targeted soldier’s android cell phones and also download another spying app that masked as an update for the particular already existed apps such as Whatsapp and get into the trap of the target persons to enable plenty of permissions to get the job done of surveillance.
Finally, in return, it empowers the hackers to implement on the demand commands, and further allow them to get the complete control on the target soldiers Android phones such as Microphone, camera, to record the conversations remotely and look into live camera footage.
On the other hand, ViperRat further empowers the hacker’s malware to steal the huge amount of the data from the targeted devices and also get access to the Geo-location, call logs, photos, text messages spy and cell phone tower information, and also get ingress into the device metadata, internet browsing and app download history.
The state-sponsored skillful hackers were able to create widespread online reconnaissance warfare by targeting the plenty of android cell phones devices of various brands such as Samsung, HTC, LG and Huawei and others.
The hackers had to get their hands on more than 9000 files from the targeted android cell phones devices were identified by lookout researchers that were actually highly encrypted images that were captured using the cell phone camera.
Moreover, Defense Forces were not the only target. The cyber-attack campaign has launched in the month of July last year, the Kaspersky researchers stated that.
Is Hamas operating at the back end?
Defense Forces officials have their watchdog with the support of Kaspersky Labs & Lookout to make a check on the issue and have made a theory that Hamas was operating these malicious attacks at the back end, Anyhow, the researchers doubted it regarding that theory.
The lookouts researchers further added that the overall module structure of code and use of cryptography protocols such as (AES & RSA encryption) the attackers were quite sophisticated.”
Researchers further added that the Hamas is not famous to be quite sophisticated cell phone abilities; it means they cannot directly involve in the spread of ViperRat.
The IDF, on the other hand, is still closely watching and working with the lookout & Kaspersky to trace out the infected targets and to prevent the further attacks, but their only single way to combat against ViperRat: don’t use apps that have come from trustless third-party sources.
