 Cloud computing and hybrid cloud have offered organizations an incredible leg up when it comes to data management and storage capabilities. As a result, the adoption of cloud technology by businesses of all sizes continues to increase. With that adoption, however, comes many considerations, perhaps the most important of which is risk versus reward. In today’s digital landscape, cybersecurity risks are an everyday fact of life but, as with most things in life, if you have policies and guidelines in place around cloud computing, security risks are definitely manageable.
Cloud computing and hybrid cloud have offered organizations an incredible leg up when it comes to data management and storage capabilities. As a result, the adoption of cloud technology by businesses of all sizes continues to increase. With that adoption, however, comes many considerations, perhaps the most important of which is risk versus reward. In today’s digital landscape, cybersecurity risks are an everyday fact of life but, as with most things in life, if you have policies and guidelines in place around cloud computing, security risks are definitely manageable.
Cloud security threats can come from a number of sources. A data breach is one of the most heavily publicized fears amongst cloud users, though data loss, whether the result of a breach, or due to human error, is also a concern. What many IT pros are now realizing is that encrypting data before it even goes into the cloud is a key strategy to implement so as to strengthen security. If you have the expertise in-house to ensure this encryption process is correctly undertaken, that’s great. If you don’t, it’s probably not a bad idea to consider working with a managed service provider vendor partner to make sure you’re properly protected.
Whether you’re an IT pro doing this on your own or working with a managed service provider (MSP), here are six best practices to put into place for your data encryption processes.
- Take Responsibility Into Your Own Hands
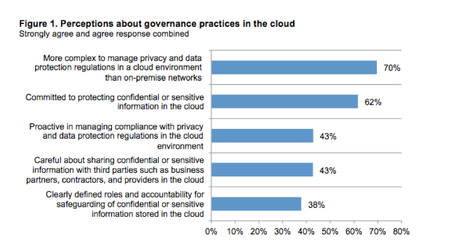
A study by The Ponemon Institute of more than 1,800 IT professionals, titled “The Challenges of Cloud Information Governance: A Global Data Security Study,” showed 71 percent of respondents believe it is more difficult to use conventional security practices to protect sensitive data in the cloud. Instead, it found that IT departments often rely on encryption and multi-factor authentication to safeguard their data in the cloud.
Also, “only 38 percent of respondents say their organizations have clearly defined roles and accountability for safeguarding of confidential or sensitive information in the cloud and 57 percent say their organizations are not proactive in managing compliance with privacy and data protection regulations in the cloud environment. Similarly, 57 percent do not agree their organization is careful about sharing sensitive information with third parties such as business partners, contractors and providers in the cloud environment.”
Well, that’s nightmare-inducing, and completely underpins the importance of having someone on the inside of the organization with the ability to monitor the cloud and work in tandem with a managed server provider to maintain security. Ideally, an internal staff member knowledgeable enough about your systems and internal requirements would be great to have. However, if you don’t have that capability in-house the right MSP can deliver the services you need in that regard. No matter what, make sure you know who is doing what and that you’ve got all bases covered.
- Look at Encryption for Data at all Points of Use
While it is obvious to consider the safety of your data when it is being transferred to and from the cloud, there are other times when it can be under threat. Typically, there are three modes in which your information will remain; in transit, at rest, and in use. In the old days, data in transit was at a huge risk, but that was before ethernet switches, when hackers could “sniff” traffic in transit. Today, data in transit isn’t without a few vulnerabilities—experienced hackers can try to gain access to what is known as a “root account” where they can spy on your server while data is in use—so there are IT folks who still insist on encrypting internal network traffic in the hopes of guaranteed security.
However, as TechTarget.com explained recently, data at rest is where the real gold is: “From a hacker’s point of view, data at rest—the data in your databases and file systems stored on your NAS, SAN and file servers—is what’s much more attractive. It’s where the “money” is—that is, credit cards, social security numbers, intellectual property, financial information and so on. The things we can’t afford to lose are what the malicious hackers and rogue employees are trying to take from us.”
Which brings us to the real elephant in the room. How to protect data that is “in-use”, or living in the cloud. Encrypting is great…until it has to be “un-encrypted” so that a business can access it and make changes. Enter “homomorphic encryption.” IBM are innovators in this technology, and, while it’s early days and a little too heady to get into deeply in this piece, here’s a good wired.com article to give you a bit of the backstory. Suffice it to say, “homomorphic encryption” is groundbreaking when it comes to securing data in the cloud.
- Avoid Old Encryption Ciphers
Algorithms such as the Data Encryption Standard (DES) are outdated and are at a much higher risk of being breached by hackers. Look to new solutions such as the Advanced Encryption Standard (AES). This also means that you should be aware of updates in encryption standards and any breaches that may occur. This is where an MSP can provide great benefit, as part of what they bring to the table is a team that’s always up-to-date on the latest technology and solutions that work across multiple industries. If you are an MSP, this should be a key selling point for you as you work with prospective clients.
- Prepare for Internal Breaches
It’s probably important to trust your employees, but you also need to prepare for a worst case scenario—before it happens. Perform regular “fire-drills” and mock breaches to make sure your encryption is strong enough to ward off potential attacks. This also means being cautious with who you provide with access to your data. Some of the largest breaches in recent headlines occurred as a result of breaches on the vendor side of the equation, but caused great liability for the companies relying on those vendors and their security measures. There’s no such thing as too much training! Train your employees on cyber-security issues and how to use encrypted data. Even those who don’t mean to put sensitive information at risk may unintentionally do so if they’re working in an area which has an issue with Shadow IT.
- Strengthen Your Key Security
If you allow a cloud provider or security vendor access to your keys, you may be giving hackers something to target. Make sure you use a form of key security that is proven and reliable. Many vendors will recommend virtual key management. This allows encryption to remain in place even when the data is in-use. Two keys and an encrypted master are given to the owner, and it means that even if theft occurs, the data will remain inaccessible. It is also recommended that you use the longest encryption keys that you are able to support. If possible, shoot for at least a strength of 512 or higher.
Remember that attackers tend to target the weakest point of any security system. When the keys can be stolen, it doesn’t make sense to try and crack a complicated encryption algorithm – they’ll just go for the keys. So ensure your organization has the control.
- Encrypt Your Backups
Another important consideration, and one that’s often overlooked, is to make sure that you encrypt your backup data as well. If you have to manage multiple copies of your data, remember that deleting the key will be equivalent to deleting all copies of the data.
Bottom line, when you’re venturing into the cloud, don’t underestimate the importance of encryption as it relates to your data. Remember that almost all encryption solutions will result in an impact on performance, whether this is increased latency or a drop in functionality. What’s important for an organization is either have the expertise in-house to properly protect your data, or to work with a managed service provider to help choose the solution that best fits your budget and security needs. If you’re a managed service provider, remember that data security is pretty much table stakes these days, so regularly communicating that value-add to your customers, as well as to prospective customers who are evaluating MSPs with whom to partner, can be a key point of differentiation.
Ultimately the strength of an encryption system is all dependent on probabilities. The more you know about encryption, the more systems you put in place, to both prepare for an attack and to ward one off, and the more you focus on safety, ultimately, the more secure you will be. A word of warning that shouldn’t be necessary, but is worth saying nonetheless: Trying to do any part of this with a DIY mindset is just asking for problems—and with the security of your data, the security of your clients’ confidential information, and perhaps even your employees’ confidential information at stake, it’s not worth rolling the dice when it comes to safety.
When it comes to the adoption of cloud technology and all the benefits it offers, a safety first mentality is going to save you many headaches. Have you migrated some of your operations to the cloud yet or are you in the process of doing so? What tips for encryption safety do you have that I might have missed or challenges have you faced that we could learn from? I’d love to hear more.
Additional Resources on this Topic:
Maximum Security: Essential Tools for Everyday Encryption
Using ‘Bring Your Own Encryption’ to Secure Cloud Based Data
Five IT Security Claims You Can Quit Believing
This post was brought to you by IBM for MSPs and opinions are my own. To read more on this topic, visit IBM’s PivotPoint. Dedicated to providing valuable insight from industry thought leaders, PivotPoint offers expertise to help you develop, differentiate and scale your business.
photo credit: Linux password file via photopin (license)

