Security is rare on the web nowadays. The government is monitoring such a large amount of the web under the U.S. Patriot Act and the projects of different governments that enable them to perceive what sites you are visiting, your identity sending messages to and what you are stating to them and whatever other data that goes through servers around the world.
Despite the fact that a few programs can erase the trail that PCs abandon when perusing, that doesn't shield you from protection totally on the grounds that that site demands all still need to experience your neighborhood network access supplier (ISP). That is the reason the P2P Proxy Network exists, to give you the protection that you need and merit, yet aren't currently getting.
What is P2P Proxy Network?
If you are web expert, you presumably know a couple of things about how data goes around the web, yet you probably won't know the entire story. Seeing how data moves to start with one PC then onto the next over the World Wide Web will enable you to ensure yourself better in the future. That begins with understanding why a reverse proxy administration like this one is so stunning and how it furnishes you with the greatest measure of security.
A proxy server is one that gets to the web for your benefit, without your own IP address regularly getting to be involved with the transfer procedure. With the way that getting to the web typically works, your IP address is signed on pretty much every webpage that you visit and when you download or transfer data. Basically, any of the sites that you got to will realize that you have been there, which pages you took a gander at, and for how long.
List Of Top P2P Proxy Servers In 2019
Luminati gives the P2P arrange offered by Hola. Luminati is a fruitful business proxy service that gives shared (P2P) proxy service has more than 16 million private IPs. Furthermore, Luminati scrambles the majority of the traffic by HTTP/HTTPS demands through a huge number of IPs.
Luminati likewise gives free VPN to utilize named hola. Hola works similar to Tor that exchanges your traffic crosswise over various Tor client's PC or servers. Along these lines, there is no free lunch in this world. Typically, Free client of Hola, by and large, goes about as a conceivable proxy hub for clients of Luminati.io. That implies what number of Hola clients have, what number of IPs that are Luminati offer.
Hola's P2P network is very huge and it contains millions of private residential IPs, unlike the other proxies. The IPs of Hola network are private and they are unlikely to be blocked or betrayed.
Features:
The most extraordinary component of Hola's P2P networks is that these networks give a huge number of nodes in each city on the planet. Today, Luminati is the only proxy that gives this sort of service. Luminati offers an API that is the most advantageous and also it is the savviest proxy solution which likewise spares a lot of time.
The fail rate of Luminati is less contrasted with different proxies. Luminati has a fail rate beneath 1%. Fail rate demonstrates the IPs that are obstructed by the site which the client is seeking. When one of the IPs is obstructed the client needs to change over to another IP and subsequently, the procedure turns out to be progressively costly.
At the point when contrasted with Luminati, different proxies are discovered more costly because of higher disappointment rates. The clients need to burn through a huge number of dollars all the more consistently because of increased fail rates with different proxies.
Why fail rate of Luminati is so low?
In the case of different proxies, the IPs are now recognized. When known IPs are utilized, they will be effectively recognized just as blocked. The private IPs that are utilized by the P2P proxy system of Luminati are not known and subsequently, they can't be recognized or blocked.
Since Luminati is utilizing private IPs, the fail rate is always underneath the 1% level. The task course of events, just as the freshness of data, is additionally affected by the failure rate. Thus, the financial limits arranged with the help of proxies with higher fail rates will lead operational hazards.
Luminati guarantees protection from misleading data
The proxies that are utilizing IPs which are easy to identify are probably going to get wrong or misdirecting data since on recognizing the IPs the site will destroy the data reaping process by giving misleading data.
This can lead to irreparable damage to the brand and will also lessen the profitability of the business. Since Luminati does not utilize known IPs but rather utilizes just private IPs, they can't be identified and thereby guarantees insurance from misleading information.
Pricing
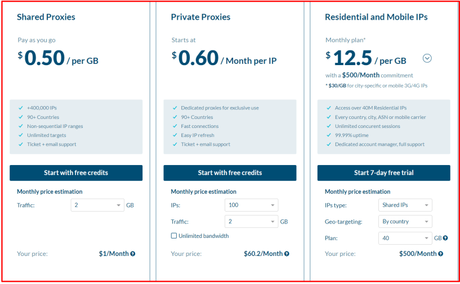

- Shared Proxies: $0.50/per GB
- Private Proxies: $0.60/Month per IP
- Residential and Mobile IPs: $12.5/per GB
Squid is a full-included web proxy store server application which gives proxy and reserve administrations to HyperText Transport Protocol (HTTP), File Transfer Protocol (FTP), and other prevalent system conventions. Squid can execute reserving and proxying of Secure Sockets Layer (SSL) demands and storing of Domain Name Server (DNS) queries, and perform straightforward reserving.
Squid likewise bolsters a wide assortment of storing conventions, for example, Internet Cache Protocol (ICP), the Hypertext Caching Protocol (HTCP), the Cache Array Routing Protocol (CARP), and the Web Cache Coordination Protocol (WCCP).
The Squid proxy store server is a brilliant answer for an assortment of proxy and reserving server needs, and scales from the branch office to big business level systems while giving broad, granular access control instruments, and checking of basic parameters by means of the Simple Network Management Protocol (SNMP). While choosing a PC framework for use as a committed Squid storing proxy server for some, clients guarantee it is designed with a lot of physical memory as Squid keeps up an in-memory reserve for expanded performance.
Squid is a Unix-based intermediary server that stores Internet content more like a requestor than its unique purpose of the starting point. Squid underpins storing of a wide range of sorts of Web objects, including those got to through HTTP and FTP. Reserving every now and again mentioned Web pages, media records, and other substance quickens reaction time and decreases transmission capacity blockage.
A Squid intermediary server is by and large introduced on a different server than the Web server with the first records. Squid works by following item use over the system. Squid will at first go about as a delegate, essentially passing the customer's solicitation on to the server and sparing a duplicate of the mentioned item. In the event that a similar customer or different customers demand a similar item before it lapses from Squid's reserve, Squid can then promptly serve it, quickening the download and sparing transfer speed.
Web access Providers (ISPs) have utilized Squid intermediary servers since the mid-1990s to give quicker download speeds and lessen inertness, particularly for conveying rich media and spilling video. Site administrators as often as possible will put a Squid intermediary server as a substance quickening agent, reserving much of the time saw substance and facilitating loads on Web servers. Content conveyance systems and media organizations utilize Squid intermediary servers and send them all through their systems to improve the experience of watchers mentioning programming, especially for burden adjusting and taking care of traffic spikes for famous substance.
Squid is given as free, open-source programming and can be utilized under the GNU General Public License (GPL) of the Free Software Foundation. The squid was initially intended to keep running on Unix-based frameworks however can likewise be kept running on Windows machines.
The squid was initially an outgrowth from the Harvest Project, an ARPA-financed open source data get-together and capacity instrument.
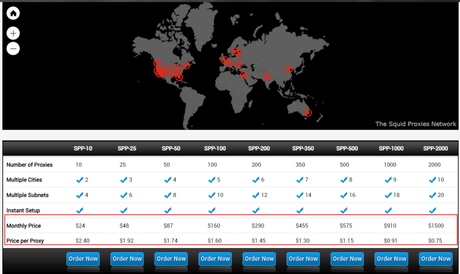
Pricing
Microleaves is another popular proxy network in the market. The Private IP is available in batches of Microleaves. All proxies come right with a 99.99% uptime they were able to handle the most difficult challenges of middle management.

With Microleaves unlimited and fast data transfer options, you will also have effective support groups for all kinds of proxies. Microleaves offers Shared Proxy and Backconnect Proxies.
Four services are offered: disconnect proxy, dedicated HTTP proxies, shared HTTP proxies, and automatic captcha resolution with independent plans and costs for each administration. All locations are effectively open without geo-containment. Customer service is done tirelessly and that's quite impressive.
Features:
- 3-day money back guarantee
- 99% Uptime Guarantee
- The IP addresses gave are genuine IP addresses a
- Offers the speed at 1 GBPS with boundless data transfer capacity.
Pricing Plans:
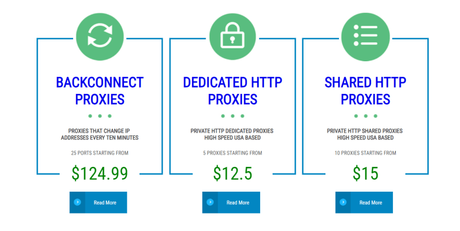
- Backconnect Proxies ($124.99)
- Dedicated HTTP Proxies ($12.5)
- Shared HTTP Proxies ($15)
Oxylabs is one of the oldest and most reliable technology companies that specialize in proxy servers. Oxylabs essentially helps companies extract important business data. The best thing about Oxylabs is that it has a pool of 1 million IP data centers and 10 million private IP proxy networks resident in more than 180 countries around the world and that's quite impressive.

In general, Oxylabs provides IP addresses for data centers and households that support HTTP / HTTP protocols and SOCKS® protocols. Let's get information about the IP addresses of the data center and the private proxy.
Data center IP: This is an IP address that is normally owned by one of the secondary companies and is not owned by any of the Internet Service Providers (ISP).
Residential Proxy: this is an IP address that is essentially assigned to one of the owner's standard Internet access providers (ISPs).
Features Of OxyLabs:
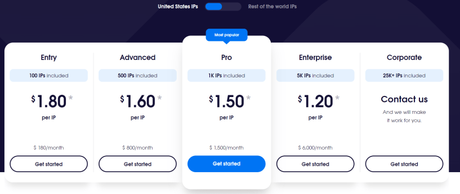
Pricing Plans:
My IP Hide is an extremely fast proxy service to unblock sites and conceal your genuine IP by encoded traffic. It is steady, quick and simple to utilize. With our upgraded proxy innovation, My IP Hide is a lot quicker than other conceal IP innovation, for example, VPN, SSH proxy and web proxy.

In the interim, it is more secure than customary proxy as a result of its scrambled traffic. With My IP Hide, you can visit any site, (for example, Facebook, Twitter, Youtube, Netflix, and BBC iPlayer) whenever and anyplace. Your record can be utilized on the Windows, Mac and Android form of My IP Hide.
You can say that free proxies are usually slow, unstable and dies fast. Sometimes it takes too much time to find new working proxies every day.
The product My IP Hide can spare your time (life). It utilizes private proxy servers. They oversee and tune them to guarantee they are continually working and quick.
- Security: Free proxies are available to open use. It makes them insecure and dies quick. On the other hand, My IP Hide is in every case quick and stable.
- Encryption: Normal proxies don't scramble their traffic. On the other hand, My IP Hide scrambles its traffic to sidestep the most exceptional firewalls.
In addition, My IP Hide is multiple times quicker than the VPN. You can peruse this test report for more subtleties. It changes IP every minute with 70 private proxies in 24 countries.
Features of My IP Hide proxy
- All bundle plans incorporate boundless information exchange, IP switches, and synchronous associations. It's multiple times quicker than VPN.
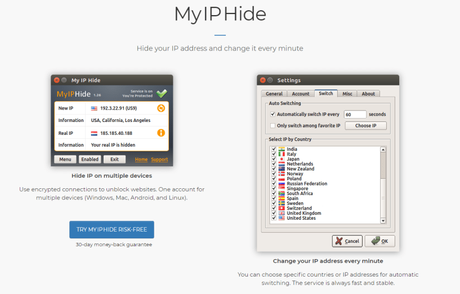
- One permit for boundless gadgets, including Windows, Mac OS X, and Android. We don't constrain the synchronous associations.
- Locally perfect with every one of the programs, including Chrome, Firefox, Internet Explorer, Edge, and Safari, requiring no manual settings.
- You can try My IP Hide, If you are not satisfied with their service, they offer a 30-day money-back guarantee on all their plans without any question, fees and hassle.
Pricing
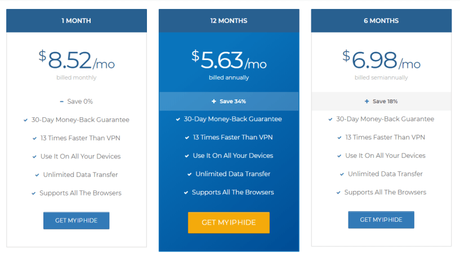
- 6 Months - $6.98/month
- 12 Months - $5.63/month
What is a Reverse Proxy Server Backconnect?
A reverse proxy, otherwise called an "inbound" proxy is a server that gets demands from the Internet and advances (proxies) them to a little arrangement of servers, typically situated on an interior system and not straightforwardly open from outside. It's "invert" on the grounds that a customary ("outbound") intermediary gets demands from a little arrangement of customers on an inner system and advances them to the Internet.
A reverse proxy can be utilized to permit confirmed clients to access an intranet notwithstanding when they are situated outside. Clients on the inner system can get to intranet servers legitimately (their IP address is their verification), however clients outside it must conform themselves to the intermediary server (as a rule with a username and secret key) so as to be permitted in.
By and large, switch proxy servers go about as burden balancers for the servers behind it. Burden balancers assume an essential job in giving high accessibility to organize administrations that get expansive volumes of solicitations. At the point when a turn around intermediary performs load adjusting, it disperses approaching solicitations to a group of servers, all giving a similar sort of administration. Along these lines, for example, an invert proxy load adjusting Web administrations will have a bunch of Web servers behind it.
The two sorts of proxy servers transfer solicitations and reactions among source and goal machines. Be that as it may, on account of turn around proxy servers, customer demands that experience them ordinarily start from the Internet, while, on account of sending proxies, customer demands regularly originate from the inner system behind them.
Features of the P2P Proxy Network
There are a ton of incredible features of the P2P Proxy Network. The most vital is the one that they have been talking about, gaining access to the servers that they have access so you are constantly anonymous. You send data to one of their proxy servers and it exits out the opposite side by means of a totally extraordinary proxy server with a totally unique IP address. That implies that you generally have another IP address. Remember, we have somewhere in the range of 20,000 to 50,000 dynamic proxy servers running at some random time, and we have a pool of 1,000,000 proxy servers that we can utilize when required. That is the reason this PSP Proxy Network is the main anonymizer on the web. Here is a portion of different features.
- Both HTTP and HTTPS will be bolstered on the majority of their hardware
- There is simply one entry point but thousands of exit points to give you unbanned IP address from different areas
- A totally mysterious proxy server that is prepared for scraping
- You will get an alternate IP address with each and every request
- The included application makes it very simple to deal with your web proxy traffic
- They have the most financially savvy answer for anybody in the business.
- They have servers in many various nations all over the world
Benefits of Using a P2P Proxy Service
A reverse proxy service is an additional layer of security for you when you browse the web. It is an untraceable path for you to browse any part of the web you pick and it is inconceivably worthwhile when contrasted with conventional proxy transferring.
In a conventional proxy server setting, the way of information would resemble this:
YOUR COMPUTER speaks with the PROXY SERVER which at that point speaks with the WEBSITE you are endeavoring to visit. YOUR COMPUTER and the WEBSITE never really meet without the utilization of your "middle man" the PROXY SERVER. The drawback here is that you can, in any case, follow the trail of information back to your unique PC on the off chance that you truly needed to.
With a reverse proxy, the communication goes like this.
YOUR COMPUTER speaks with the PROXY SERVER which at that point speaks with a mysterious, continually changing SECOND PROXY SERVER which at that point speaks with the site you are endeavoring to get to. YOUR COMPUTER and the PROXY SERVER are in correspondence, and the PROXY SERVER and the SECOND PROXY SERVER are in correspondence, however, the second proxy doesn't have any thought what is on the opposite side of that unique proxy server. That implies that you are totally untraceable.
There are numerous advantages that accompanied surfing the web namelessly, yet the greatest one is the way that you can reclaim your entitlement to security. You likely won't have a gigantic requirement for security when you're doing customary web surfing, viewing Netflix or browsing your email, yet with one of the most minimal estimating structures out there, you could without much of a stretch use P2P Proxy to browse the web full-time.
What is an Anonymous proxy server?
Anonymous proxy servers don't exchange the data about your genuine IP address. That implies you resemble a phantom on the Internet. No one has even an idea about your genuine area and in this manner, they can't set up illicit associations with your PC for data taking purposes.
The main POSSIBLE disservice could be the way that site you are perusing could realize that you utilized a proxy server for association (you may concealing your IP address). From the other hand, if a client utilizes a proxy server that does not constantly mean he is attempting to shroud his genuine IP address. At times, similar to when you are utilizing versatile WAP Internet, all clients are compelled to utilize a proxy server for their associations (essentially for observing purposes).
That is the reason the way that you are utilizing a proxy server for association now and then will be treated as would be expected conduct and mysterious intermediary server will securely conceal your genuine IP.
Instructions to Protect Your Internet Privacy
Obviously, this information is covered under a huge number of different clients and it is typically not an issue since it would take a lot of work to uncover everything from underneath there, and just for nothing, on the off chance that you weren't doing anything on the web you wouldn't need anybody to see.
Yet, stop and think for a minute: just because the chances are endlessly small that somebody will really recover your logs and just because that you are doing nothing incorrectly; regardless it attacks your privacy. It doesn't make a difference where you go on the web; you deserve the right to surf without anybody seeing where you are going. That is the place a proxy server like P2P Proxies Network comes in.

Whether you need to hide your online activities as a business substance or for individual reasons, the switch proxy process is the most ideal approach. The servers that we make accessible are all best in class innovation that is suitable for business or home use.
A proxy server is similar to a cover for your PC. Nobody realizes that it is you surfing any of the destinations that you are visiting since everything they can see is the proxy server. Yet, that is just how an ordinary proxy server functions. P2P Proxies' reverse proxy service makes it a step further. The proxy server that you are utilizing sends the data to another intermediary server, picked totally at irregular, to complete the request . This implies that you truly surf the web totally secretly.
It implies that each time you send a solicitation for data, it will originate from a totally new, randomly picked IP address, out of our pool of somewhere in the range of 1000 to 2000 that are dynamic at some random time. Altogether, we have about 1,000,000 proxy servers and are continually switching things up.
If you somehow happened to utilize a similarity that was proper for what this administration does, a statement from the well-known novel Harry Potter and the Prisoner of Azkaban does it justice; attempting to seize your data trail when you utilize their service is like "trying to get smoke with your bare hands."
Quick Links:
Conclusion: List Of Top P2P Proxy Servers In 2019
There are a ton of extraordinary features of the P2P Proxy Network. The most crucial is the one that we have been examining, gaining admittance to the servers that they have access so you are constantly mysterious. You send information to one of their proxy servers and it exits out the opposite side by means of a totally unique proxy server with a totally extraordinary IP address.
That implies that you generally have another IP address. Remember, they have somewhere in the range of 1,000 to 2,000 dynamic proxy servers running at some random time, and they have a pool of 10,000 intermediary servers that they can utilize when required. That is the reason this P2P Proxy Network is the main anonymizer on the web. Here is our top recommendations:
We hope this post suits your purpose well. if you liked the post then you can share it on various social media channels like Twitter, LinkedIn, and Facebook.


