 In a world of tight healthcare budgets and increasing pressure to implement new technology, many healthcare CIOs are looking to the cloud for solutions. The flexibility and potential cost savings that cloud services can offer are obvious benefits to healthcare executives facing ever-higher costs to collect, collate, and store vast amounts of digital data.
In a world of tight healthcare budgets and increasing pressure to implement new technology, many healthcare CIOs are looking to the cloud for solutions. The flexibility and potential cost savings that cloud services can offer are obvious benefits to healthcare executives facing ever-higher costs to collect, collate, and store vast amounts of digital data.
But, we’re talking healthcare here. The highly regulated health sector comes with heavily monitored security and privacy guidelines and regulations, challenges that CIOs in the commercial sector simply don’t face.
Those challenges come from regulation requirements under the Health Insurance Portability and Accountability Act (HIPAA), which impose obligations on healthcare services, and often to those who provide cloud computing services to them. For many in the field, these obligations have been a roadblock, and perhaps even a disincentive to make changes, especially digital ones.
Technology is moving fast though, and the pressure to change, adapt, and adopt new ways of doing business in the healthcare space isn’t going to go away. Even the most reluctant to embrace change and new technology will ultimately have to migrate to the cloud and master HIPAA compliance and security in the process.
HIPAA: Then and Now
Before looking at how that can be achieved, let’s explore a little of the background and provide some context around how we got to where we are today. HIPAA was introduced in 1996 to regulate the use and disclosure of health information. The legislation has four main thrusts:
The Privacy Rule: Protects the privacy of individually identifiable health information.
The Security Rule: Sets national standards for the security of electronic health information.
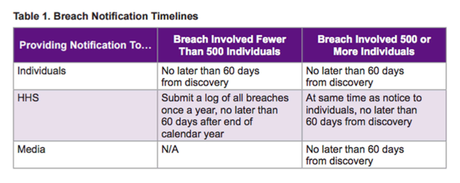
The Breach Notification Rule: Requires notification to the authorities following a breach of unsecured health information (see table below). Courtesy of the Department of Health and Human Services
The Patient Safety Rule: Protects identifiable information that’s being used for analysis and research.
Although initially covering only those who provide treatment and/or payment and operations in healthcare (referred to as “covered entities” (CE)), a 2013 update to the act also included those with access to patient data who provide support (referred to as “business associates” (BA)). This latter category is wide ranging and includes providers of managed IT and cloud computing services, which also must comply with the act.
This means that the healthcare provider, its managed IT services provider and/or cloud service provider, and any subcontractors need to be aware of the requirements HIPAA and have the appropriate safeguards in place. Which of course is a good thing—as the security and safety of private health data is of the utmost importance.
What Does it Take for a Cloud Host to Be HIPAA Compliant?
Great question. A cloud host must have specified administrative, physical, and technical safeguards in place, including:
Physical safeguards. Physical safeguards covers facility access and control, with policies covering use and access to workstations and media.
Technical safeguards. Technical safeguards covers access to electronic protected health data including user IDs, encryption, and emergency access procedures.
Technical policies. Technical policies covers integrity controls, IT disaster recovery, and offsite backup policies.
Audit controls. Audit controls include audit or tracking logs, which are required to be maintained so as to identify the source of any violations.
Network controls. Network controls are critical. Systems must protect against unauthorized access during transmission of data including email, Internet, and other networks.
The HIPAA Omnibus Rule and the BAA
In a rapidly evolving and maturing cloud market, vendors are already emerging that claim to have the capability to handle all of these stringent requirements, but it makes sense to approach these relationships with a caveat emptor strategy.
Entities for whom it is critical to be HIPAA-compliant and are looking to engage the services of a cloud partner would be remiss to simply hand over responsibility for HIPAA to a third party. The HIPAA Omnibus Rule, which added responsibilities for business associates in 2013, makes it clear that a covered entity is liable for the acts of its agents, including business associates.
So handing over HIPAA compliance to a vendor comes with much responsibility for the covered entity healthcare provider. In fact, since September 2014, CEs and BAs have been required to enter into a written Business Associates Agreement (BAA).
The BAA sets out the basis for the relationship between the two parties including:
- Establishing the permitted uses and required disclosures of protected health information (PHI).
- Stipulating that the BA must use appropriate safeguards to prevent unauthorized PHI uses and disclosures.
- Sets reporting procedures for any unauthorized uses and disclosures.
- Confirms the extension of the terms of the BAA to subcontractors.
- Establishes that upon termination of the BAA, the vendor must either return or destroy all PHI.
Beyond the agreement, the BA-managed IT service vendor partner should also have comprehensive systems in place to ensure that information is properly protected. The CE should be actively involved in vetting this process, as this extract from the guidelines on the American Health Information Management Association (AHIMA) website makes clear:
“The BA must have a carefully constructed set of privacy and security policies and procedures. These policies and procedures should be reviewed by the CE as part of the contracting process. Policies should cover employees, volunteers, contractors, and other members of the BA workforce, as defined by HIPAA.”
So the BAA as well as any supporting written policies and procedures or other service level agreements are important indicators of the service a health provider may receive from a managed IT services and/or cloud technology provider.
As ever, the devil is in the details, so attention to the small print is critical. Particular attention should be paid to factors such as attitudes towards privacy, the location of data and any consequent implications, data ownership, data access, and procedures in case of payment defaults or the vendor ceasing to trade.
Going into any arrangement that might lead to a “lock-out,” or loss of control over data could prove to be a catastrophe for any HIPAA-regulated business.
Questions for Potential Vendor Partners
So, if you’re in healthcare IT, you know how all this HIPAA compliance business can make a head spin. If you’re a provider of managed IT services, hopefully you are aware of all the sticky issues involved in HIPAA compliance and just how careful a healthcare provider and its IT team must be in identifying the right vendor partner. In addition to what’s been discussed above, some additional factors that need to be carefully investigated and considered include things like:
- Is end-to-end data encryption available?
- What backup arrangements are in place? It may be prudent to have secondary cloud or on-site backup for watertight protection.
- What firewall and intrusion detection systems are in place?
- Has a risk analysis been undertaken and if so, what were the results?
A review of documentation provided by potential partners, supported by further questions of specific areas of concern, can reveal a great deal and help to refine which managed IT and cloud service providers offer the most secure and efficient service.
The Cost of Noncompliance is Steep
As you likely well know, ensuring HIPAA compliance isn’t just a one-off check of a box. It’s an ongoing process of monitoring, training and, most importantly, taking action when failings are identified. The HIPAA regulations stipulate that failure to act in a case where a BA is not compliant is an act of willful neglect, with each violation punishable with fines up to $1.5 million. Add in the potential for fines of up to $50,000 per day for breaches of patient data, and you can see that failing to live up to HIPAA expectations can be a very costly.
Cloud computing can offer many benefits to health organizations in terms of scalability, flexibility, and cost. Employing third-party associates in the health sector does, however, bring with it additional layers of complexity and responsibility that must be fully understood. Mastering HIPAA compliance and ensuring the security of patient data in the cloud are essentials for all healthcare professionals, their IT teams, and the vendor partners who serve them. When it comes to HIPAA compliance and security in the cloud, there is no room for error.
Have you been involved in HIPAA compliance issues, either in health IT or as a provider of managed IT and cloud services? What are the biggest challenges you’ve faced? I’d love to hear your thoughts on this and any tips based on your experiences thus far.
Additional Resources on this Topic:
Key to HIPAA Compliance is Understanding Your Data Center and Cloud Risks
Managing the Data Security Risks of Patient Portals
Cloud Computing: Data Protection in Healthcare Industry
This post was written as part of the Dell Insight Partners program, which provides news and analysis about the evolving world of tech. For more on these topics, visit Dell’s thought leadership site Power More. Dell sponsored this article, but the opinions are my own and don’t necessarily represent Dell’s positions or strategies.
Photo Credit: AZ Laptop Medic via Compfight cc

