The world is amid a pandemic—there an environment of distress, threat, and uncertainty all the time. Many countries are stuck in lockdown as it is one of the most efficient ways to break the chain of the outbreak and prevent community spread.
All companies and services are shut, and all employees have been strictly advised to work from home.
In such a scenario where the majority of people are working from home, the popularity of online communication platforms & social media platforms has gone up significantly. During the lockdown, more and more content is being generated and viewed by users.

In the wake of the outbreak, Zoom has become immensely popular as more & more people are looking for platforms to hold virtual meetings. The popularity of this videoconferencing software also is attributed to its cloud-based communication platform that can be used for audio and video conferencing, online meetings, chatting, and options to hosts webinars.
And it is this popularity and spike in usage of Zoom that the cybercriminals are trying to take advantage of. They are registering hundreds of new Zoom domains for malicious purposes. These hackers are seeing the work from home paradigm shift as an opportunity to deceive, trap, and exploit people.
According to the recent Check Point Research report, over 17,000 new domains have been registered in the past few weeks. Out of these registered domains, 4% contain suspicious characteristics.
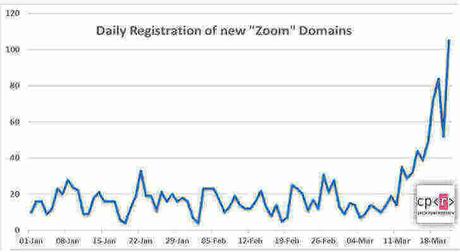
Malicious files using a zoom-us-zoom_##########.exe have also been discovered. When these are executed, they launch an InstallCore installer that potentially tries to install unwanted third-party applications and malicious payloads.
Security and privacy updated
Zoom was always on the vulnerable side. There were some significant privacy and security issues since the last year. And this year, they finally updated their iOS app after it was caught sending device information to Facebook’s server. They’ve now removed Facebook SDK from their application to prevent any data loss and transmission.
You must safeguard yourself and beware of such threats; just keep that all your apps are up-to-date, and keep an eye on the sender of the emails. DO NOT open any unknown attachments or promotional links in the email.
Just stay safe from Corona and threats like this!

