Enterprise mobility helps appreciably in simplifying and automating complex business processes, leading to increased efficiency and exceptional monetary benefits. Be it healthcare, education, media & entertainment or almost any other field, mobility has cast a magical spell with simple, sophisticated and sound solutions to the otherwise strenuous tasks. However, with all these advantages, the booming trend also gives rise to severe information security concerns.

Information security threats in enterprise mobility
Alongside providing diverse benefits, enterprise mobility also runs the risk of getting affected by several security threats:
Mobile Threats: These could be of many types such as:
- Targeted Trojans: Distributed through phishing mails, these malware collect and upload sensitive user data such as contacts, SMS, call records, apps, etc., at the hacker’s end.
- Mobile spyware: What apparently seems to be a legitimate mobile app, could turn out to be a harmful malware. For example, the malware Android /Roidsec.A that pretends to be an app to sync user mobile device, actually transfers sensitive information including call logs, contacts, messages, etc., to the hacker’s server.
- Banking Malware: Users in Asia and Europe generally have to undergo a two-factor authentication for secure access of user account and to prevent the attacker from intrusion. Attackers can bypass this authentication to steal username and password from the user’s device.
General Malware Threats:As per the Q1 2013 report by Pandasecurity, there has been a steep increase in the growth of general malware threats. The report reveals that above 6.5 million malware samples surfaced right in the first quarter, with Trojans (74.46%) doing the bulk of scoring. In the 2nd quarter, the percentage of Trojan infections (77.2%) increased even further. Other malware to create ruckus for enterprise mobility included Rootkit, Ransomware, and so on.
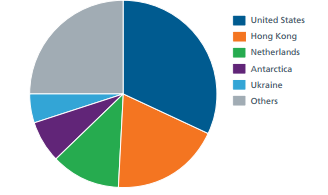
Network Threats: According to McAfee Global Threat Network, the United States leads both in terms of infecting the web with malware, as well as being the target of malware. As compared to 1st quarter of 2013 (44%), the browser-based risks mount to 73% of the total attacks in the next quarter. The same holds for PDF-based attacks where US dominates with 53% threats as compared to 35% in the previous quarter, the report says. Taiwan and China are the next to follow the suit.
Web Threats: The McAfee report reveals 12% increase in the number of suspect URLs as they exceed by 64 million compared to the Q1, 2013. Among these include 27.7 million domain names, showing an increase of 6% from last quarter. Not surprisingly, the US yet again has emerged as the major hub of these threats as it hosts 94% of all the phishing and spam URLs and included malware, malicious codes, and exploits.
Messaging Threats: The volume of spam messages crossed an unprecedented 2 trillion mark in April 2013. This indicates the gravity of security threats, messages could cause to enterprise mobility. Among the countries to be at the receiving end of spam messages, Ukraine and Belarus topped with a staggering 200% increase since the last quarter.
BYOD Threat: Though not a malware, the BYOD concept could well be the reason behind malware infection in the sensitive corporate data. If the prediction by Gartner is to be believed, around 50% of the total companies across the globe would follow the “Bring Your Own Device” (BYOD) phenomenon by 2017 thereby eliminating the dependence of users on corporate-owned devices for work. While this comes out to be as respite for the workers, organizations need to take additional measures to secure their data from malware attacks.
Other threats: Among other threats to mobile security may subsume absence of a foolproof security strategy, limited IT control, loss of data due to the theft of gadget, improper security solutions, etc.
Dealing with information security threats
The burgeoning volume of malware indeed poses severe threat to information security of individuals and businesses. Stiff measures are hence desired to combat the growth of all the malicious activities, paving the path for intrusion free data across enterprises.
The Approach
Some important points that corporates may consider while devising strategy for information security include:

Source: Appbuilderwiz
- Securing the device as well as the entire data path, i.e., from the mobile app to data center.
- Protecting devices, servers and all the other communication points from internal and external security risks.
- Connecting only the authenticated mobile app users.
- Providing customized security, which protects user instead of the device.
- Safeguarding the device and data from Bluetooth/wireless hacking, geo-location tracking, general privacy and ownership threats and physical thefts.
Likewise, certain security measures could also be assessed during various stages of mobile app project life cycle itself, such as:
- Requirements: Data handling, end to end security elements.
- Architecture and design: Platform and infrastructure security.
- Construction: Manage application data using best tools and API’s.
- Testing: Threat modelling, eavesdropping and data exfiltration.
- Deployment: Follow App store guidelines, implement policies, updates and certificates.
Securing BYOD Program

Source: Securedgenetworks
To establish BYOD security, the foremost need is to create a strong policy that could achieve the intended objectives yet maintain utmost secrecy for the organizations.
Some of the important considerations while devising BYOD policy may include:
- Who will pay for the mobile device?
- What rules should be followed while leveraging the devices?
- What measures could be taken to secure the devices?
- Whether the data on the BYOD devices would be in the cloud, or on a local server?
- Will the employees need to go through an agreement before bringing a personally owned device?
- What will happen if a worker goes against the BYOD policy?
To summarize, enterprise mobility is a boon for the existing and future entrepreneurs as it exploits the power of mobility to connect with maximum customers worldwide. However, despite its many benefits, the trend may get a major setback owing to lapses in information security in the current mobile apps and devices. Strict measures are hence a necessity to make sure that the data remains secluded from the attackers throughout the data path traversal – from the corporate/BYOD device to data center.
Finoit cares to implement utmost security to the mobile applications it develops, enabling its clients to safeguard data confidentiality of their customers. Throughout the mobile app development life-cycle, we assesses all the necessary security measures and implements them accordingly. Be it to create Android, Windows Phone or iOS app, the company utilizes upscale tools and technologies to incorporate the best data security measures.
To know more about our services or to seek our assistance in your coveted app development projects, feel free to approach our mobile app development company India.
- About
- Latest Posts

Siya Carla
Siya is a social media enthusiast with a background as Web and UI designer, and is Social media manager of Finoit. She has deep inclination towards writing about emerging technologies,Web and Mobile app development and other technology related stuff.
Latest posts by Siya Carla (see all)
- How Is Location-Based Marketing the Best Mobile Strategy? – October 4, 2016
- For Your App’s Success, 7 Mobile App Tests you should Try NOW! – September 27, 2016
- iMessage App Store – What Does It Mean for a Marketer? – September 15, 2016
