Cybersecurity is the most integral part of any organization. CyberArk is a popular tool that offers information security. It is used to reduce security risks without increasing operational complexity. It addresses the problem of securing privileged credentials, access keys, and secrets on the cloud or on-premises. It provides a secure way for users to access these credentials. If you are interested in learning CyberArk, you can take our CyberArk training course.
The most trending topic in the market right now is that the Kubernetes security issues were disclosed by CyberArk. So what exactly is Kubernetes? And what security-related loopholes did CyberArk find out about Kubernetes?
First of all, Kubernetes is an open-source platform to orchestrate containers. It is a cluster of nodes or machines running containerized applications. Kubernetes containers won’t be tied to individual machines. Users will be able to deploy, scale, and manage applications in containers. When you deploy applications in Kubernetes, it maintains a state, which specifies which applications should be running. When you set a state for your cluster, Kubernetes will automatically manage your cluster according to your specified state. You can automatically scale the cluster based on load using Kubernetes patterns.
What did CyberArk do?
CyberArk has focused on taking care of the security aspect of Kubernetes. CyberArk has tested the Kubernetes and says that cybercriminals might exploit and compromise the Container Network Interface (CNI) security. CNI is used to connect Kubernetes Pods. A pod is the smallest and simplest Kubernetes object, which is a set of containers that are deployed in a single node. A kubelet is an agent software that is used to create containers and has full control over pods. When we create new pods, kubelet is responsible for monitoring the state of the pods and containers. It reports back the status back to the API server regularly. A kubelet treats all requests as anonymous without rejecting any request. This makes the kubelet unsecure in a default Kubernetes installation. Kubelet has its own direct API that has no connection to the Kubernetes API and lies over port 10250/TCP by default.
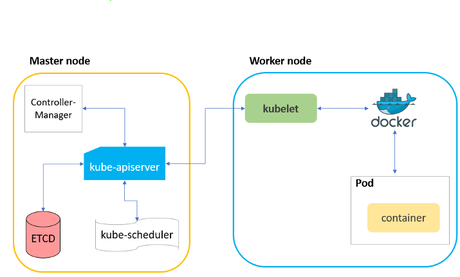
How did CyberArk do it?
CyberArk has created a client that makes anonymous requests, a “kubeletctl” tool. The “kubeletctl” is a new open-source CLI client for kubelet that implements all the kubelet APIs. It is built to make the run commands easier without using CURL. It will be able to scan all the open kubelet ports. We can communicate directly with the kubelet API from the “kubeletctl” tool.
To test the vulnerability of kubelet, CyberArk has performed penetration testing. It has tested the default port 10250/TCP to attack Kubernetes cluster. To check what information we can extract, they identified an accessible kubelet API. The /pods endpoint has given the list of pods along with their namespace and container details. Now that we have the pods and container details, we can run commands inside them. Through the “kubeletctl” tool, we can run any commands on all pods without having to define a specific pod and container. One more thing that the attackers will be interested in is the token information. The “kubeletctl” tool even has a search command (kubeletctl scan token) through which we can get a list of all the tokens from all containers.
How can we mitigate attacks on Kubernetes pods?
CyberArk has specified that the way to protect the Kubernetes default installation is through changing some configurations. First, we have to disable anonymous requests to the Kubelet server. Next, we should not allow all requests and enable explicit authorization. This way, attackers won’t be able to access the pods and the containers. You can configure these settings either in the kubelet configuration file or while running the kubelet executable. IT teams should ensure that DevSecOps processes include policies and procedures for securing Kubernetes infrastructure. If you don’t want to deal with the settings and installations, you can directly use the managed Kubernetes services like Azure AKS AKS, AWS EKS, kubeadm, etc.
Recommended Reading :
- Why Every Enterprise Needs a Robust Cybersecurity Strategy
- 7 Ways to Reinforce Your E-Commerce Site’s Cybersecurity
- Vulnerabilities have Dramatically Increased in 2020
- 6 Effective Steps to Carry Out Penetration Testing Successfully
- What is the Significance of a Network Security Audit for a Business
- Apply These 7 Tips to Protect Your Online Business
Conclusion
One thing that we need to keep in mind is that there are a lot of hackers out there that have already tried scanning for open kubelet ports. There have been records that Kubernetes clusters have been compromised before. These attacks might not slow down the adoption of Kubernetes but the IT teams do face some challenges. Developers always assume that the default installation of Kubernetes is secure. The IT teams should make sure that the kubelet configuration is configured properly to make it secure.
Author Bio
Chekoti Swathi, Technical graduate in computer science engineering, Digital Marketing professional at HKR Trainings. Aspires to learn new things to grow professionally. My articles focus on the latest programming courses and E-Commerce trends. You can follow me on LinkedIn.
