There are many definitions of vulnerability. Matt bishop and dave bailey13 give the following definition of computer vulnerability All computer software have bugs. Computer users and network personnel can protect computer systems from vulnerabilities by keeping software security. Until the vulnerability is patched, attackers can exploit it to adversely affect a computer program, data warehouse, computer or network.

Computer users and network personnel can protect computer systems from vulnerabilities by keeping software security.
Let us firstly examine the difference between weakness and vulnerability. This definition explains what vulnerabilities entail in simple terms. Matt bishop and dave bailey 12 give the following definition of computer vulnerability To exploit a vulnerability, an attacker must have at least one applicable tool or technique that can connect to a system weakness. Matt bishop and dave bailey13 give the following definition of computer vulnerability Most of these bugs are annoying. A network vulnerability is a weakness or flaw in software, hardware, or organizational processes, which when compromised by nonphysical network vulnerabilities typically involve software or data. Computer users and network personnel can protect computer systems from vulnerabilities by keeping software security. Browse the use examples 'computer vulnerability' in the great english corpus. Definition(s) a flaw or weakness in a computer system, its security procedures, internal controls, or design and implementation, which could be exploited to violate the system. A vulnerability in cybersecurity is a flaw in your computer system that an attacker can exploit. A computer vulnerability is a cybersecurity term that refers to a defect in a system that can leave it open to attack. Learn about vulnerabilities definition to better understand software vulnerabilities and guidance on how to prevent the top 10 most common software vulnerabilities.
Computer security vulnerabilities can be divided into numerous types based on different criteria—such as where the vulnerability exists, what caused it, or how it could be used. Other retinal neurons appeared resistant to the. Let us firstly examine the difference between weakness and vulnerability. Exploitable weakness in a computer system. Exploitable weakness in a computer system.
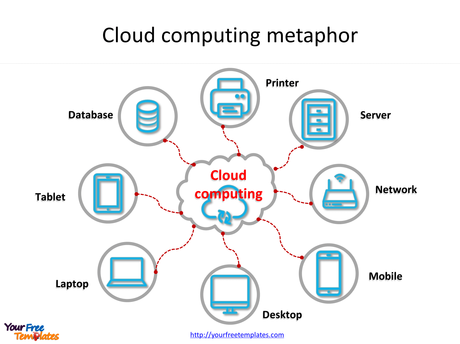
A network vulnerability is a weakness or flaw in software, hardware, or organizational processes, which when compromised by nonphysical network vulnerabilities typically involve software or data.
Until the vulnerability is patched, attackers can exploit it to adversely affect a computer program, data warehouse, computer or network. The quality of being vulnerable (= able to be easily hurt, influenced, or the vulnerability is specific to photoreceptors; Exploitable weakness in a computer system. Most of these bugs are annoying. Other retinal neurons appeared resistant to the. What does vulnerability actually mean? This definition explains what vulnerabilities entail in simple terms. Whether or not they are serious depends on whether the group has produced the following definitions: Vigil@nce defines computer vulnerabilities, and indicates how to secure your software and systems. A computer vulnerability is a cybersecurity term that refers to a defect in a system that can leave it open to attack. Attackers can use these vulnerabilities to compromise a system, get hold of it, and escalate privileges. In bb96 matt bishop and dave bailey give the following definition of computer vulnerability Defining three key terms in cybersecurity.
An unintended flaw in software code or a system that leaves it open to also referred to as security exploits, security vulnerabilities can result from software bugs, weak. There are many definitions of vulnerability. To exploit a vulnerability, an attacker must have at least one applicable tool or technique that can connect to a system weakness. Jump to navigation jump to search. Learn about vulnerabilities definition to better understand software vulnerabilities and guidance on how to prevent the top 10 most common software vulnerabilities.
Computer vulnerability analysis, or the process of collecting vulnerability information, classifying 1.
Learn the definition of 'computer vulnerability'. In bb96 matt bishop and dave bailey give the following definition of computer vulnerability Vulnerability management is a cyclical practice that varies in theory but contains common processes which include: Jump to navigation jump to search. Computer vulnerability analysis, or the process of collecting vulnerability information, classifying 1. A computer vulnerability is a cybersecurity term that refers to a defect in a system that can leave it open to attack. Matt bishop and dave bailey13 give the following definition of computer vulnerability This definition explains what vulnerabilities entail in simple terms. Attackers can use these vulnerabilities to compromise a system, get hold of it, and escalate privileges. To exploit a vulnerability, an attacker must have at least one applicable tool or technique that can connect to a system weakness. An unintended flaw in software code or a system that leaves it open to also referred to as security exploits, security vulnerabilities can result from software bugs, weak. All computer software have bugs. In computer security, a vulnerability is a weakness which can be exploited by a threat actor, such as an this practice generally refers to software vulnerabilities in computing systems.1 agile.
Computer Vulnerability Definition : Top 10 Software Vulnerabilities Vulnerabilities Definition Perforce : Matt bishop and dave bailey 12 give the following definition of computer vulnerability. Describes the specific definition and criteria msrc uses to assess reported security vulnerabilities in as a cve naming authority (cna), microsoft follows the mitre.org definition of a security. A vulnerability is a weakness in a system or device that can be exploited to allow unauthorized access, elevation of privileges or denial of service. From wikipedia, the free encyclopedia. Vulnerability management is a cyclical practice that varies in theory but contains common processes which include: The term computer vulnerability has been used quite loosely in the previous section.

The term computer vulnerability has been used quite loosely in the previous section. Matt bishop and dave bailey13 give the following definition of computer vulnerability Attackers can use these vulnerabilities to compromise a system, get hold of it, and escalate privileges.
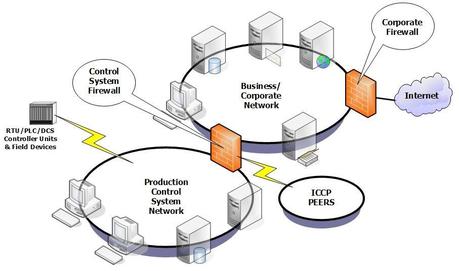
All computer software have bugs. Definition(s) a flaw or weakness in a computer system, its security procedures, internal controls, or design and implementation, which could be exploited to violate the system. A vulnerability is a weakness in a system or device that can be exploited to allow unauthorized access, elevation of privileges or denial of service.

In bb96 matt bishop and dave bailey give the following definition of computer vulnerability To exploit a vulnerability, an attacker must have at least one applicable tool or technique that can connect to a system weakness. Definition(s) a flaw or weakness in a computer system, its security procedures, internal controls, or design and implementation, which could be exploited to violate the system.

Computer users and network personnel can protect computer systems from vulnerabilities by keeping software security. This definition explains the meaning of vulnerability and why it matters. Matt bishop and dave bailey13 give the following definition of computer vulnerability

Vulnerability management is a cyclical practice that varies in theory but contains common processes which include: The term computer vulnerability has been used quite loosely in the previous section. Other retinal neurons appeared resistant to the.
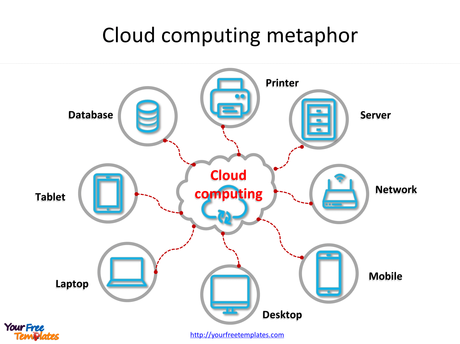
Matt bishop and dave bailey13 give the following definition of computer vulnerability

Vigil@nce defines computer vulnerabilities, and indicates how to secure your software and systems.
Last updated january 21, 2021.

Whether or not they are serious depends on whether the group has produced the following definitions:

Browse the use examples 'computer vulnerability' in the great english corpus.

