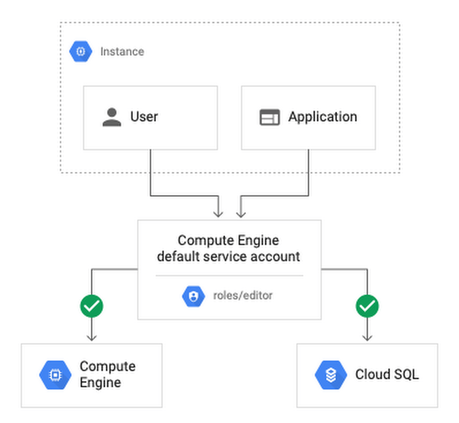
The compute engine default service account is created with the iam project editor role, but you can modify the service account's roles to securely limit which google apis the service account can. Google cloud application default credentials (adc) are not credentials. By default, all compute engine instances can run as the default service account. The default service account has the editor role and sets default auth scopes for various gcp products. My preferred way of acheiving the same result would be by using the compute engine default service account.
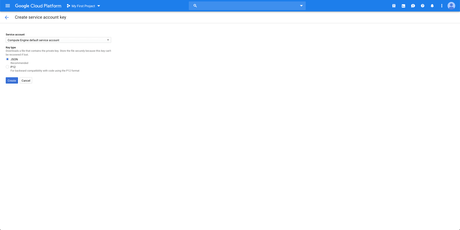
You want to make sure that the vm uses this service account instead of the default compute engine service account.
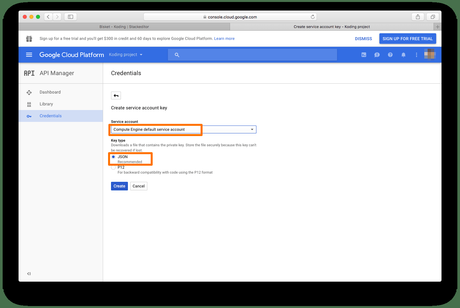
The compute engine default service account is created. Download a json private key for the service account. The default compute engine service account is not configured with sufficient permissions to access the cloud sql api from this vm. This account has broad access by default, making it. Use the credentials in the json file to log in to the vm. Depending on the application you end up creating after this codelab, you might need a physical account key which you could get on this page by hitting the create key button. You want to make sure that the vm uses this service account instead of the default compute engine service account. This way the service account is the identity of the. For example, a compute engine vm can run as a service account, and that account can be given permissions to access the resources it needs. See application default credentials for more information. The following arguments are supported: Google support told us we should be able to make requests to gae standard handlers with the default compute engine service account. That script includes a step where i use python lib google.cloud.storage to upload files in google storage.
As written in the doc, authentication should just work. I want to use the default service account of the compute engine instance. See application default credentials for more information. You created a service account with the appropriate access rights. The service account will be assigned to the compute engine instance itself which will grant default credentials for the whole instance.
Please create a new vm with cloud sql access (scope) enabled under identity and api access.
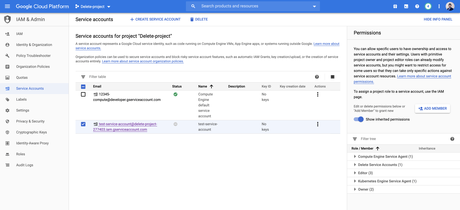
Services that run as virtual accounts access network resources by using the credentials of the computer account in the format <domain_name>\<computer_name>$. This way the service account is the identity of the. Google creates the compute engine default service account and adds it to your project automatically but you have full control over the account. Using application default credentials ensures that the service account works seamlessly; Google cloud application default credentials (adc) are not credentials. The compute engine's default service account's default scope is none for cloud sql which is consistent with the problem i experienced. The following arguments are supported: The following arguments are supported: Adc is a strategy to locate google cloud service account credentials. On google cloud, adc automatically searches for default service account when running on compute engine, app engine, kubernetes engine, cloud run, and cloud functions. Use the credentials in the json file to log in to the vm. After the vm has been created, download the json private key for the default compute engine service account. By default, nodes are given the compute engine default service account, which you can find by navigating to the iam section of the cloud console.
When creating the vm via the web console, specify the service account under the ג€˜identity and api accessג€™ section. By default, all compute engine instances can run as the default service account. Use this data source to retrieve default service account for this project. The service account will be assigned to the compute engine instance itself which will grant default credentials for the whole instance. For example, a gke cluster created with the default service account gives.
By default, nodes are given the compute engine default service account, which you can find by navigating to the iam section of the cloud console.
By default, nodes are given the compute engine default service account, which you can find by navigating to the iam section of the cloud console. You created a service account with the appropriate access rights. This snippet creates a service account in a project. When creating the vm via the web console, specify the service account under the ג€˜identity and api accessג€™ section. When creating the vm via the web console, specify the service account under the 'identity and api access' section. I run a python script hourly, embedded in a docker container hosted on a google compute engine instance. To see the service account name for the firewall instance, view the instance details and scroll to the bottom (refer to the compute engine default service account). Depending on the application you end up creating after this codelab, you might need a physical account key which you could get on this page by hitting the create key button. Services that run as virtual accounts access network resources by using the credentials of the computer account in the format <domain_name>\<computer_name>$. Adc is a strategy to locate google cloud service account credentials. The service account will be assigned to the compute engine instance itself which will grant default credentials for the whole instance. The following arguments are supported: Google support told us we should be able to make requests to gae standard handlers with the default compute engine service account.
Compute Engine Default Service Account / Google Cloud Platform Roles And Permissions - For example, a gke cluster created with the default service account gives.. This snippet creates a service account in a project. The compute engine default service account is created. By default, nodes are given the compute engine default service account, which you can find by navigating to the iam section of the cloud console. The following arguments are supported: After the vm has been created, download the json private key for the default compute engine service account.

You want to make sure that the vm uses this service account instead of the default compute engine service account. You want to configure an ssh connection to a single compute engine instance for users in the dev1 group. That script includes a step where i use python lib google.cloud.storage to upload files in google storage.
Then, on the servlet, i would rely on the userservice to check whether the request is coming. The compute engine default service account is created with the iam project editor role, but you can modify the service account's roles to securely limit which google apis the service account can. This way the service account is the identity of the.
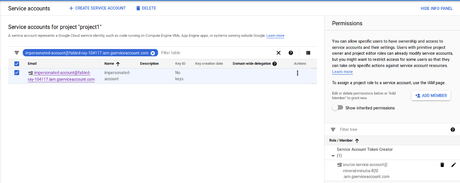
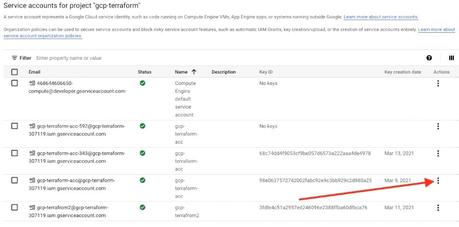
Then, on the servlet, i would rely on the userservice to check whether the request is coming. You created a service account with the appropriate access rights. To recover the service account (within 30 days), you would need to find it's unique id using cloud logging.
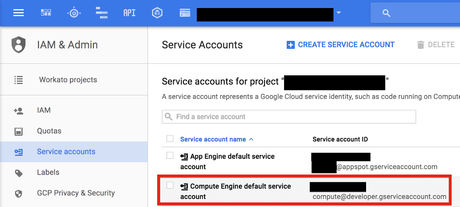
Please create a new vm with cloud sql access (scope) enabled under identity and api access. The compute engine default service account is created. This service account might be a default service account provided by compute engine, google kubernetes engine, app engine, cloud run, or cloud functions.
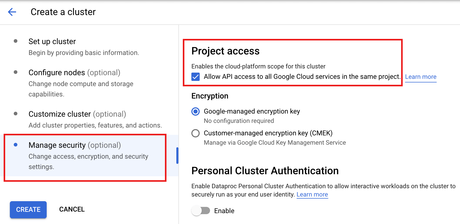
Download a json private key for the service account. This account has broad access by default, making it. Google support told us we should be able to make requests to gae standard handlers with the default compute engine service account.
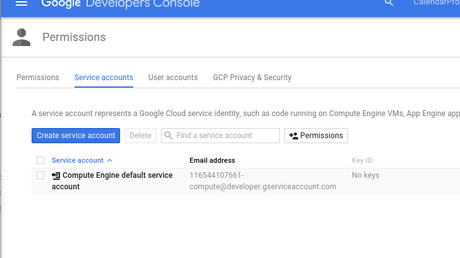
If the environment variable google_application_credentials is set, adc will use the filename that the value contains for service account credentials.
If the default value is used for the service accounts during sql server setup, a virtual account using the instance name as the service name is used, in the format nt service\<servicename>.
The compute engine default service account is created with the iam project editor role, but you can modify the service account's roles to securely limit which google apis the service account can.

Use the credentials in the json file to log in to the vm.
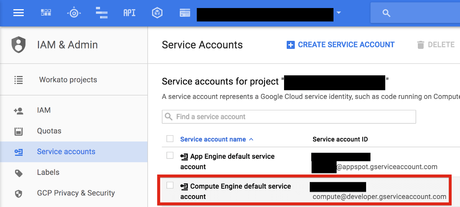
The service account will be assigned to the compute engine instance itself which will grant default credentials for the whole instance.

