 Without question, CIOs of organizations of all sizes have their hands full when it comes to dealing with Shadow IT. The way to keep your sanity (and your organization) secure is with regular cloud maturity assessments. How did we get there? Well, back in the days before anyone had heard much about cloud services, the role of the CIO and the IT department was pretty clear; they sourced, installed, and maintained the technology that powered the business. Now though, the waters have been muddied by the proliferation of easily accessible SaaS services, which allow other departments to source their own out-of-the-box solutions without the need to involve in-house IT. This technology transformation, which presents unintended and unforeseen risks to the business in terms of cost and security, is one that CIOs must assess and control, not just as a one off, but as a vital part of their standard operational procedures.
Without question, CIOs of organizations of all sizes have their hands full when it comes to dealing with Shadow IT. The way to keep your sanity (and your organization) secure is with regular cloud maturity assessments. How did we get there? Well, back in the days before anyone had heard much about cloud services, the role of the CIO and the IT department was pretty clear; they sourced, installed, and maintained the technology that powered the business. Now though, the waters have been muddied by the proliferation of easily accessible SaaS services, which allow other departments to source their own out-of-the-box solutions without the need to involve in-house IT. This technology transformation, which presents unintended and unforeseen risks to the business in terms of cost and security, is one that CIOs must assess and control, not just as a one off, but as a vital part of their standard operational procedures.
The Extent of Shadow IT in Business
It’s pretty much a given that within any organization unauthorized (and/or unknown) cloud usage is generally higher than what any CIO might estimate. The extent of the problem was well illustrated by a survey carried out last year by Vanson Bourne, who questioned 200 IT decision makers (ITDMs) and 200 business decision makers (BDMs) across the U.S. and U.K. (of companies with 1,000 employees or more), to find out more about how so-called Shadow IT is affecting business. The results reveal clear differences in the perceptions of IT leaders with their peers, and shows that the growth of rogue IT is undoubtedly going to continue at a rapid pace. Here are some insights from the study:
- More than half (55 percent) of business decision makers said that Shadow IT is prevalent in the majority of departments within an organization, compared to just 37 percent of IT decision makers.
- Less than half of ITDMs believe Shadow IT has been a feature in their organization for two years or more, compared to more than two-thirds of BDMs.
- Just over half (51 percent) of ITDMs said that they think the use of Shadow IT will increase in the future; nearly three-quarters (71 percent) of BDMs said that they expect their department to commission more.
- The use of shadow IT is being driven at the highest levels within an organization, with 76 percent of BDMs saying that it is department heads or senior managers who are making the decisions.
It’s NOT About Money
The thing that jumped out at me from this survey is that the use of Shadow IT isn’t at all predicated on cost. Senior level executives are driving the adoption of various forms of cloud-based technology and they are doing it because they feel it makes their teams more productive and more efficient. It allows them to do what they need to do more quickly and easily and to get what they want, when they want it. Isn’t that what we all want? This snapshot from the infographic produced on the results of this study shows the differences in perceptions on this between business development managers and IT department managers—and they are quite different perceptions indeed.
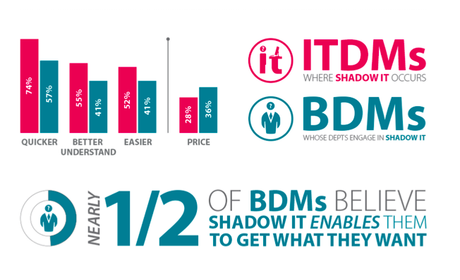
As you can see from the above, almost six in ten (57 percent) of BDMs said that they believe the use of Shadow IT makes their department more productive and more efficient. An even higher proportion (61 percent) said that they were making life easier for their IT colleagues by freeing up the IT departments time. It’s not a stretch to say that the CIO and/or IT team in general might well disagree with that.
Interesting stuff, isn’t it? What we’re clearly seeing is that many department heads are no longer prepared to go through the process of getting the go ahead from the IT department before finding, buying, and deploying a solution that they think will work for them. Cloud-based software is readily available, often at low cost, ready to deploy with no infrastructure or maintenance requirements, and leaves no footprints on company owned devices.
Oh, the Inherent Security Risks
It’s easy to understand the temptation. Shadow IT solutions will generally be sought and implemented with the very best of intentions, as well as the welfare of the organization, (or at least the welfare of that specific department and its goals), in mind. What can’t be denied though is that the use of Shadow IT impacts data security in a big way, it impacts budgets in a big way, and it impacts the effectiveness of the IT team and their ability to serve the interests of both the company and the work force in the most effective manner possible. This is where the perceptions of BDMs and the reality of ITDMs differ greatly.
As you can see from the graphic below, 85 percent of ITDMs believe shadow IT presents a risk to the organization’s security, with almost half describing that risk as either extremely significant or their most significant risk. Conversely, only about 33 percent of BDMs consider shadow IT a risk to the security of the organization. Clearly a case of you don’t know what you don’t know—which is more than a little frightening.

What CIOs Can do From Here: Assess Consumption On a Regular Basis
The changes in the ways that IT is being consumed requires a changing role for the CIO, who needs to be less of a builder of IT systems and more of a broker of cloud services. Taking on the role of “cloud manager” means they can better anticipate and meet the needs of their own internal customers, while at the same time taking back control of security, compliance, and financial risks.
Before any of that can be done though, the organization needs to know the extent of the adoption of Shadow IT within the organization, and understand the motivation behind a decision by a department or division leader to go rogue in the first place. The way to make that happen is to do an internal assessment. That means establishing an inventory of cloud apps in use, examining the patterns in the way they are used, and then analyzing the extent of the risks they present. Whether carried out using third-party tools, working with a managed service provider, or by internal processes, there are certain questions that must be asked as a part of this assessment.
These include:
- What cloud services are in use and are they effective in supporting the needs and goals of the department and/or the business?
- Are there cloud services that are redundant and can be dispensed with?
- What are the risks inherent in the use of each cloud application and what are the data and security policies of the providers?
- How much is the business spending on cloud services, can savings be made, and would consolidation strengthen negotiating power to reduce costs?
- How are the cloud services managed and what service level agreements are in place?
- What were the perceived benefits to the department that led to them bypassing IT in the first place?
- How can we address those perceived benefits and service the department(s) involved in a better way moving forward, removing the desire for separate solutions?
Once this baseline has been established, CIOs and their teams will have the information they need to convince their C-Suite colleagues of the benefits of a more coordinated approach. Only then can the drive to convince employees that cloud services should come out of the shadows and under the umbrella of IT begin. Does the process stop there? Definitely not! The ease with which cloud services can be deployed, and the attraction to employees of using services that they are familiar with in their personal lives won’t go away. That’s why cloud consumption assessment must be an ongoing process and become standard operational practice.
If left unchecked, Shadow IT has the potential to be a ticking time bomb for businesses and organizations. IT departments and CIOs need to adapt to meet the challenge and retain control of technology and, in the process reduce the risks and costs involved in the use of cloud computing. That’s why, whether you’re a CIO, an IT pro, or a managed service provider focused on the needs of your clients, knowing where the organization is (or your clients are) with regard to cloud consumption is something that must be benchmarked and regularly monitored. In a nutshell, cloud consumption assessment needs to be built into the culture and not considered as a one-off, or even worse ignored altogether.
How does your organization deal with the threat of Shadow IT? I’m always interested in what’s happening within your various organizations and how you’re dealing with the challenges of keeping your arms around Shadow IT. And if you’re not in IT, but instead are one of those senior leaders who has taken matters into his or her own hands with regard to a cloud-based technology solution, is it delivering the results you anticipated?
If you want to see the full infographic, which pretty much boils down the findings of the research at a glance, check it out.
Other Resources on this Topic:
The Perils of Shadow IT: Your Most Senior Executives Are Doing It [Ask Hillary]
Cloud Apps: Just How Many Does Your Firm Use? Now Guess Again
Research Shows 40% of Cloud Users Using Unsanctioned Apps
This post was brought to you by IBM for MSPs and opinions are my own. To read more on this topic, visit IBM’s PivotPoint. Dedicated to providing valuable insight from industry thought leaders, PivotPoint offers expertise to help you develop, differentiate and scale your business.
Photo Credit: Ivan Pierre via Compfight cc

