 The contemporary world is interconnected with each other in terms of computing devices and it has served us in various aspects of our lives and made it quite easier. However, the modern wireless world also has made us vulnerable to the cyber-security attacks to the fullest. Nowadays, nothing is impossible to hack, form cell phones, laptop and desktop computer machines, cars, and even the tube lights. But the very dangerous threat is appearing about implanted medical devices. Moreover, experts have demonstrated which security on pacemakers even the insulin pumps are possible to breach which are more likely to result in brutal and dramatic consequences.
The contemporary world is interconnected with each other in terms of computing devices and it has served us in various aspects of our lives and made it quite easier. However, the modern wireless world also has made us vulnerable to the cyber-security attacks to the fullest. Nowadays, nothing is impossible to hack, form cell phones, laptop and desktop computer machines, cars, and even the tube lights. But the very dangerous threat is appearing about implanted medical devices. Moreover, experts have demonstrated which security on pacemakers even the insulin pumps are possible to breach which are more likely to result in brutal and dramatic consequences.
Laurie Pycroft, Ph.D. Candidate, University of Oxford
The researchers of Oxford Functional Neurosurgery have written in the paper about the security threats in the form of brain implants. “Unauthorized control of brain implants or “brainjacking” has been scientifically fictionalized over the last couple of decades and with the continuous advancement in the technology is making it possible.
Cyber-Security Threat as Deep Brain Stimulation
The deep brain stimulation (DBS) system is one of the most common brain implants or brainjacking. It is based on the implanted electrodes fixed deeply inside and the brain attached to the human wires placed under the skin that take signals from the stimulator fixed in the brain.
On the other hand, the stimulator contains the battery, tiny processor and last but not the least wireless communication antenna that empowers the doctors to program it. It is characterized as more likely to the cardiac pacemaker, with its exception of being directly connected with the brain.
Deep brain stimulation DBS system is capable to do the treatment of multiple disorders. It is one of the effective ways to cure the Parkinson’s disease, and often ended up with dramatic results and further, it is also considered best to treat dystonia, necessary tremor and against severe chronic pain. However, it is also suitable for the conditions of the patient being with depression and with Tourette’s syndrome.
How Brain Stimulators Cyber-security Threat?
The ability to target multiple regions of the brain alongside different kinds of brain stimulations parameters enables neurosurgeons to get control over the human brain to eradicate the distressing symptoms. So, the control on the brain with such a precision wireless by controlled stimulators rises opportunities for malicious cyber-attackers to go beyond the limits to control insulin pumps or cardiac implants into the territory of profoundly concerning attacks.
Remote Control Cyber Security Threats
There could be plenty of examples of possible remote control cybersecurity attacks include altering stimulation settings. Therefore, the particular patients with chronic pain or the caused severe pain would feel without the stimulation. Moreover, when it comes to the Parkinson’s patient may have the ability to move self –consciously. The talented attacker is more likely capable of inducing behavioral changes in terms of hyper-sexuality or pathological gambling.
However, they can remotely exercise limited type of control over the patient’s behavior through the stimulating regions of the brain based on reward learning for the sake of orders some sort of actions. Hacks are very difficult to govern, but when it comes to the high-level technological talent and power to monitor the victim, an experienced black hate hacker would more likely to manage it.
Solutions to Prevent Cyber Security Threats: Implementation at Question
The proposed solutions are the number of for the prevention of cybersecurity threats to brainjacking. All the solutions seem more resistant to the attacks online and remotely. But the makers of the devices are confused particularly for the implementation of the security features. Currently, the features of the solutions are not capable yet to the perfectly designed security system that should be used in the real –world.
The implants are consisting of the heavy battery, size and the capacity of the battery that ultimately seems not fitted. The devices are in the range of medical staff at the time of emergency because it is important to have it at crucial times. All the exciting features that likely to control the implants or brainjacking with the use of the cellphone, computers connected to the cyberspace, should enhance against the risk the particular features can cause.
Brianjacking or Brian Implants Could Rise in Cyber-security Threats
These days with the rise in the rise of technology brain implants becoming very common. It gets approved for the cure of the diseases, cheaper and with multiple features in particular to implant with a human brain. Although this is quite good, the complex and cyber-connected implants are more likely to pose serious cyber-security threats.
So, the human with the brain implants or brain jacking could be exploited by the cyber attackers and turned humans with implants into a criminal one. Let’s suppose for a while terrorist group with the experience of hacking can get access to the politician’s, mind or even can blackmail someone and control anyone’s brain to act and thin like the terrorist does.
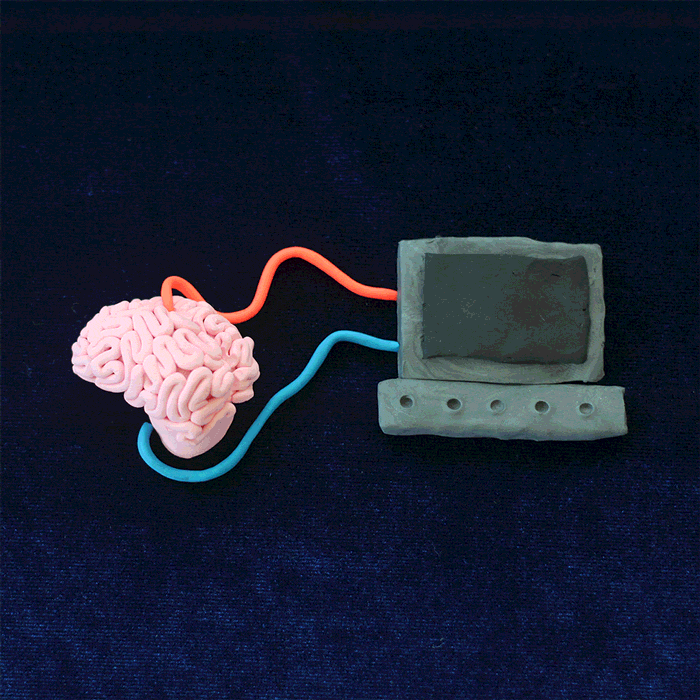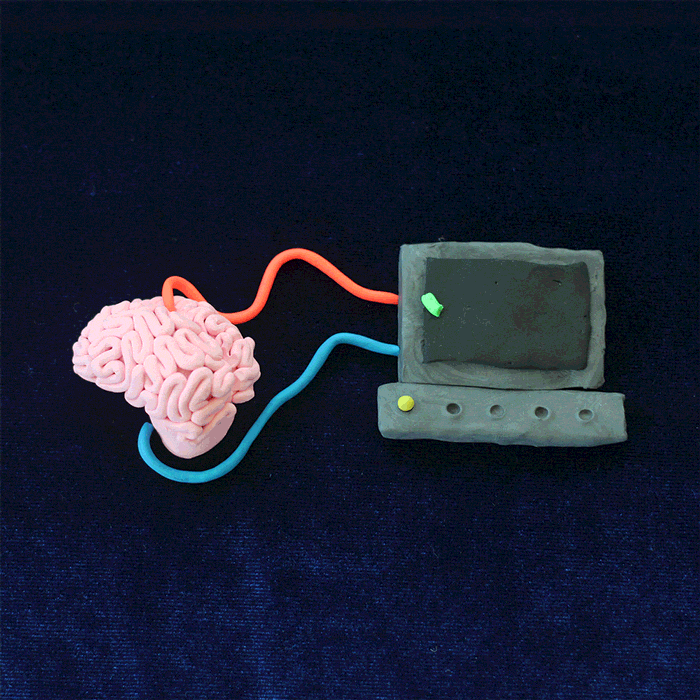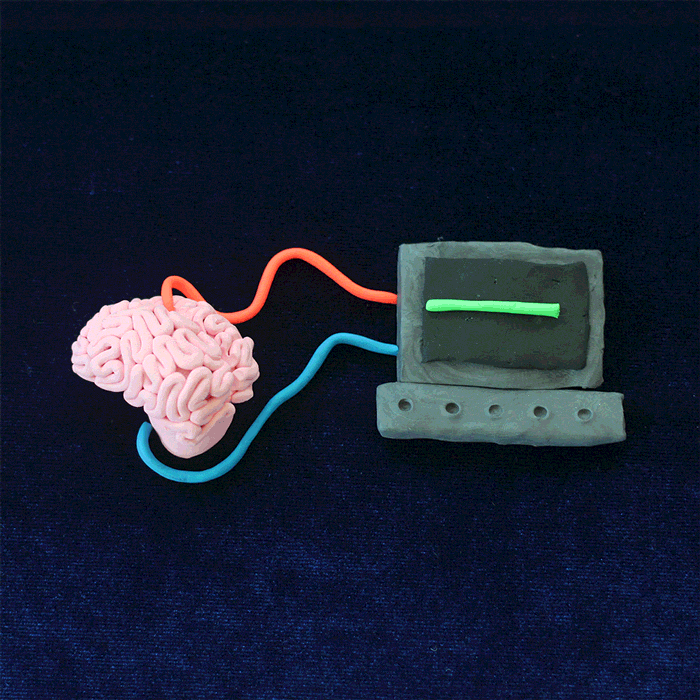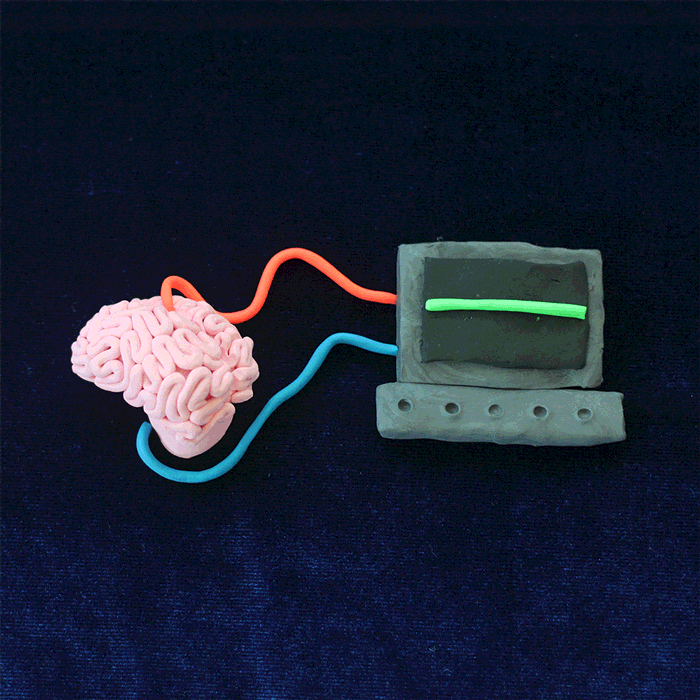
So, the brainjacking being fictionalized in the movies scientifically seems true in the upcoming future. However, it is important to know that there is no such evidence till date that suggests any kind of implant has been attacked in the real world and there is no such patient with such implants has been attacked.
No matter what, it is still a sensitive issue that we need to address and device makers, regulators, scientists and engineers, and even the doctors should think about it before it is too late.
Furthermore, the upcoming feature of neurological implants seems bright; on the other hand, a single cyber-security threat in terms of brainjacking would break public confidence on the safety and purity of the devices. So, it needs to be taken and should be addressed seriously.
