Simple question: Are you protecting your digital identity? Now, I usually don’t talk about technology; that’s Jessica Williams forte on the Girlz and Gizmos column. But something a little scary happened to me a couple of weeks ago.
Below is my twitter profile:
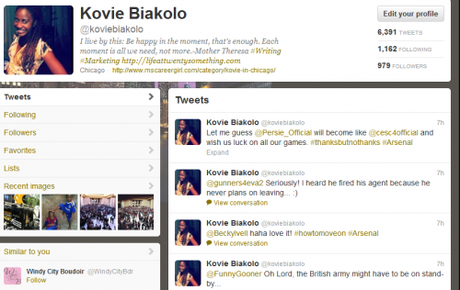
Below is a picture that I used to use as my “tweet pic.”

….And below is a picture of someone else using my former tweet pic AND my name (which is not the most common name in any part of the world including Nigeria’s Urhoboland where my family is from). The username is @Sarai580.
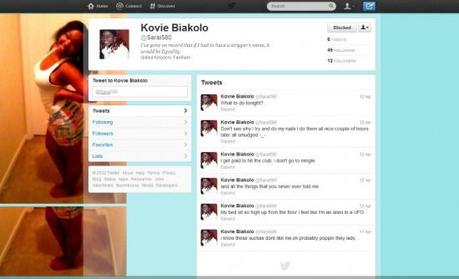
Scary, isn’t it? I’d like to think one of my friends is playing a hoax on me but seeing as none of them have come forward, it’s probably not a joke. I’d also like to be flattered but I’m not. I’m freaked out, creeped out, and wondering why on earth someone would use the name and picture of someone else who is not remotely famous. Of course, she can’t use my username, thank goodness for that, but if you search “Kovie Biakolo” – both my account and this user will come up. And because that is the name on her profile and she is using MY picture, it could be mistaken for me.
I asked all my Facebook and Twitter friends to mark the account as spam but alas, I still have to go through the twitter report process for impersonation. I have to send in some documents proving my identity and what not. It’s an annoying task that I’ve been meaning to get to but I thought I’d write this post first to get your thoughts (and hopefully your comforting lamentations of how creepy this is). So, now that this has happened, I’m a little bit paranoid, needless to say. Not necessarily about using social media or being online because that’s simply a part of my lifestyle. But I am paranoid that it could happen again or worse.
With that in mind, here are my three tips for protecting your digital identity:
1. Google yourself. And don’t just Google yourself, search yourself on all the social media sites that you have accounts on. One of the reasons I was able to find this is because I have the tendency to search myself online once in a while. What’s interesting is that this Twitter imposter hasn’t posted anything since April but I can almost swear I’ve searched myself on Twitter multiple times before I found out just a few weeks ago. So I don’t know how it all works but search yourself often. This is the digital space and employers and everyone else knows how to find your digital identity – take care of it.
2. Enable “two-factor authentication” on your Gmail account. And please don’t tell me you don’t have a Gmail account because this is 2012 and why wouldn’t you have one? Now, two-factor authentication is a mouthful and it might take you anywhere from twenty to thirty minutes to install but it’s worth it. For a much better explanation of how two-factor authentication works than I can ever give, read this Gawker article. The article also helps you set it up. Basically, if you consider that a hacker may take over your digital life including but not limited to your social media profiles, information on online stores like Amazon, wipe out all your photos… twenty to thirty minutes of your time is a small price to pay. Bonus points if you get two-factor authentication for your Facebook account. Actually, no bonus points, I HIGHLY RECOMMEND it!
3. Don’t put anything online that you wouldn’t sign your name to in real life. This is more of a reminder (I hope). I’m on just about every popular social media site, I have a blog and write on a few too, and you know why I feel comfortable doing so? Because other than this imposter here, I try to stay on top of my online identity and keep it as clean and classy as possible. Sure, there are days I want to rant, rave, and rage at people or things online but I don’t. You know why? Because It’s not worth it. I once heard that typing, uploading or commenting on something online is like walking into a room full of people and yelling your thoughts to them. If you use that analogy, you’ll think before you type.
Has anything creepy ever happened to your digital identity on social media or online? What advice do you have for people regarding their digital identity? How are you protecting your digital identity?
Tagged as: career women, digital identity, gen y, social media, twenty somethings

