Companies are scrambling to find new methods to give employees who work both in and out of the office safe remote access as the hybrid work model takes hold. The legacy VPNs of the past don't fulfill today's requirement for secure remote access, leaving enterprises susceptible to security breaches and raising the possibilities of cyber assaults across their networks.
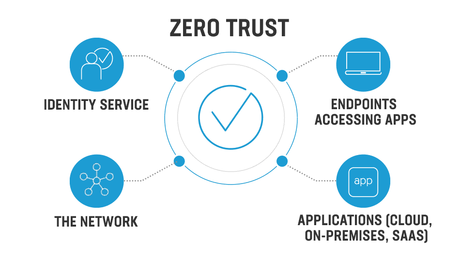
the zero-trust network access effect takes place (ZTNA). Access to on-premises and cloud resources is increasingly being separated and managed to ensure that only personnel who can be trusted have access. By applying the Zero Trust, "never trust, always verify" strategy, firms may drastically lower the attack surface and secure their important resources.
ZTNA is a bundle of security solutions that identify, authenticate and verify each corporate user, ensuring sure they have the right identification and credentials to access company addresses and services.
With ZTNA's firewall as a service, multifactor authentication, and network segmentation, administrators can monitor and control all network traffic.
Why Make the Switch the Zero Trust
1. The old VPN is being replaced with the new ZTNA.
Cyber thieves have changed their technology, why shouldn't you? The sophistication of hackers means that even the smallest error or weakness may put the data of your whole firm at risk.
Legacy VPNs don't segregate user access, so if a cunning hacker sneaks their way into your network, they have access to any and all business resources. Due to the restricted network resources available to each ZTNA user, an attacker cannot take advantage of ransomware, phishing, or other human blunders.
2. Full network monitoring and visibility
With effective network monitoring and management, you can be sure to spot any unusual behavior quickly as it happens. ZTNA solutions give monitoring reports and detailed user activity breakdowns so that you successfully identify possible dangers and eliminate troublesome individuals.
To successfully track and manage your network, you need more than a traditional VPN can offer. ZTNA goes beyond simple user statistics and reports on all network activities such as users' connected region, gateways, network, log-in time, and much more.
3. Reducing the attack surface
Segmenting access for each user so that they may only access specified corporate resources without being exposed to the network as a whole is a snap using Zero Trust. In the case of a cyber assault, a hacker can only access the restricted resources exposed to one individual user, drastically minimizing the attack surface and mitigating the harm of a data leak.
4. ZTNA for the hybrid workplace
ZTNA is a solution built for the hybrid work environment. A typical VPN doesn't give the high-speed access needed for enterprises working on-prem and in the cloud. As more employees work from home, connecting across numerous gateways and accessing cloud services requires the right bandwidth and cloud architecture needed to handle high quantities of remote workers.
With ZTNA, high-speed encrypted tunnels feed user traffic to cloud resources with little latency, guaranteeing quick and secure connectivity for your whole workforce.
5. It is accurate in terms of size.
With ZTNA, the sky is the limit when it comes to scalability. With ZTNA, you no longer have to worry about configuring and maintaining individual pieces of network hardware. Add users, build networks and offer third-party contractors access with only a few clicks. It's the all-in-one answer you've been looking for as your business expands.
You can use Perimeter 81 to secure your workplace and enjoy a seamless experience.
Restoring the Security of Remote Access
It's time to upgrade from your outdated VPN to a ZTNA-based one. ZTNA enables safer remote work, improved network administration, and increased security from online dangers. Join thousands of enterprises in securing their on-prem and cloud resources with the Zero Trust method now!

