How You Can Stay Safe
Sweeping digital revolution during the Covid-19 epidemic has transformed how individuals utilise apps and cloud-based solutions in their business and personal life. Cyber-attacks have risen as more and more new and uninformed people post their personal information online.
New data from Perimeter 81 shows that 66% of businesses will have a severe cyber event in 2021. The biggest culprit? Phishing.
To secure your organization's funds and sensitive data, it's vital to follow cybersecurity best practises that prevent phishing and other strategies for obtaining your credentials and entering your network.
What is Phishing?
Phishing is a sort of cyberattack that employs social engineering to fool people into exposing their login passwords, credit card numbers, and other private information. Sending an email that appears to be genuine and provides a link to a website where you are requested to submit your data or download an app is one way to achieve this. Keeping private information a secret sounds like a no-brainer, but social engineering strategies may be tough to uncover.
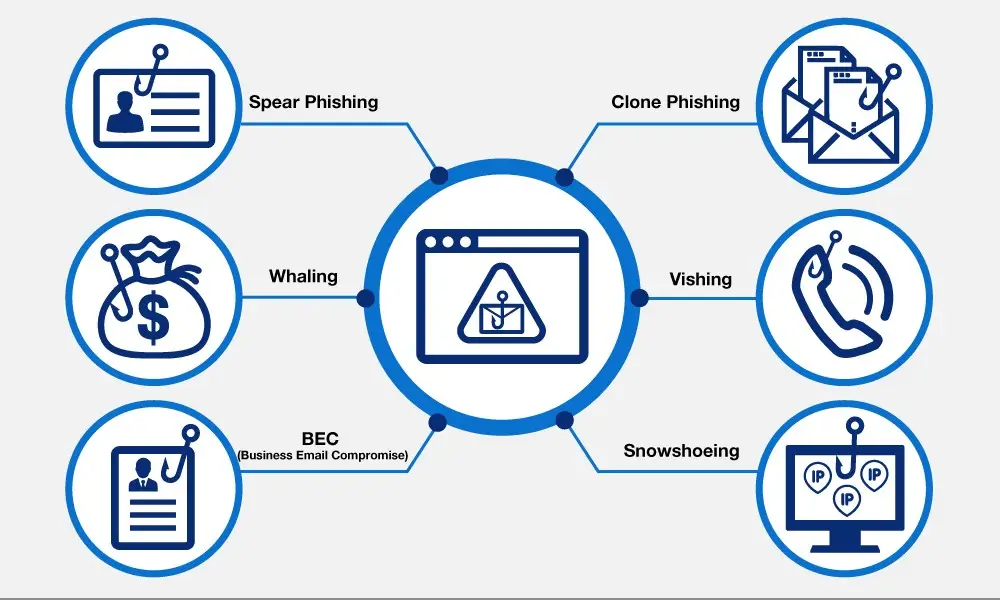
Attackers are proficient at appearing to be a trusted entity like a supervisor or a vendor, frequently employing images and links to make it look like the email is coming from a valid source. In order to steal your personal information, the scammer will lure you into clicking on a fraudulent link or email attachment that contains harmful malware.
Sometimes phishing emails are so misleading that high-level personnel are often targeted and successfully defrauded by an attacker.
How to Stay Safe From Phishing Attacks
1. Continuously engage in cybersecurity awareness training
Phishing efforts are supposed to be difficult to recognise. Fraudsters wouldn't earn any money if their techniques didn't work, and scammers are growing better at misleading employees. A recent poll indicated that 78 percent of users clicked on fraudulent links while professing to be conversant with the hazards of phishing attempts.
Continuous training on the detection of phishing emails, false websites, faked phone numbers, and other signs of fraud is vital for all employees in the firm, regardless of level or clearance.
2. Comply with cybersecurity rules
Rising cybersecurity issues paired with expanding numbers of remote employees have forced governing and regulatory authorities to re-examine their approach to security compliance in the Digital Age. Compliance requirements such as the EU's general data protection regulations (GDPR) and California's consumer privacy act (CCPA) were designed to align firms with industry standards and best practises.
Although not yet mandatory in the US, suggested cybersecurity strategies include transferring resources to the cloud and installing a Secure Web Gateway (SWG) with specified user roles. A Secure Web Gateway, like the one supplied by Perimeter81, is meant to stop illegal traffic from accessing an enterprise's network. It does this by keeping a close eye on Internet traffic and blocking any potentially harmful content.
If your business experiences a breach, PCI incident response processes can help you retrieve the stolen information and reduce the harm that happens, providing you stay in compliance with PCI DSS rules.
Implement a network access strategy based on zero trust
At its heart, a Zero Trust Network Access (ZTNA) ensures that users have safe access to only the business resources that they require and nothing else. Implementing ZTNA with Perimeter 81's Cybersecurity Experience Platform-recognized by Forrester consultancy as a top solution-can help decrease the effect of phishing attempts by micro-segmenting the pages and files that each user has access to.
If an attacker acquires business credentials when zero trust is installed, they will only have access to a tiny section of the network. In zero-trust architectures, network segmentation depends on centralised administration to improve network visibility and detect new threats before a data breach is launched.
4. Protect Your Accounts Using Multifactor Authentication (MFA) (MFA)
Multifactor authentication gives an extra degree of protection by needing two or more credentials to get access. Multifactor authentication is similar to two-factor authentication in that it does demand more than a basic username and password combination to access your online accounts.
In spite of having your login and password, phishing fraudsters can't access your accounts because of multifactor authentication, according to the Federal Trade Commission. Two-factor authentication commonly employs SMS confirmation to validate your identity and allow access.
On the other hand, multifactor authentication employs technologies like authentication applications, security keys, and biometrics to generate a unique login for every user, making it incredibly difficult for scammers to hack into your accounts. Perimeter81 supports multifactor authentication, including by SMS notification, Duo Security, or Google Authenticator.
5. Implement an SSE Solution That Is Extremely Simple
It's usual for business networks to adopt multiple security measures to decrease phishing attempts and frauds. However, 70 percent of CEOs feel that the quantity of cybersecurity technologies hurts their capacity to detect and prevent attacks negatively.
Security Services Edge (SSE) is a unified approach to cybersecurity that incorporates numerous important cloud-based security services inside one cloud-based administrative panel. Through SSE's simplified cybersecurity strategy, you may have complete visibility into all sections of the network and make discoveries to help avoid phishing and other cyber assaults from affecting your firm.
Perimeter81's Cybersecurity Experience Platform (CSX) drastically simplifies your cybersecurity by employing SSE as a guide and helps organisations to get rid of their obsolete gear. Among the many features it offers are Zero Trust Network Access, Firewall-as-a-Service, a Secure Web Gateway and others to ensure that IT staff and company personnel have secure access to the resources they require.
In Conclusion
The first step in preventing phishing scams is educating employees on how to spot them. Next, ensure that your IT infrastructure complies with current security standards and impose a zero-trust strategy that depends on multi-factor authentication in your organization's IT architecture.
Finally, make sure that you are utilizing a unified SSE solution like Perimeter 81's CSX that includes a secure online gateway, ZTNA, and integrative capabilities to safeguard your most precious assets.

