 Many companies are headed to the cloud these days looking for new and better ways to collaborate, store, and share information. Is yours? Whether you’re going the public, private, or hybrid route, moving to the cloud is a very popular decision—in fact, you’ll find 93 percent of companies share your strategy. Of course you didn’t adopt cloud because you wanted to jump on a bandwagon, you did it because of the myriad benefits this new type of data storage brings to an organization. But, how well did you assess privacy issues? What about the very real potential for a company security breach that results in the loss of sensitive data? Did you train your staff well enough? How confident are you that your shared documents are fully protected against a cyberattack?
Many companies are headed to the cloud these days looking for new and better ways to collaborate, store, and share information. Is yours? Whether you’re going the public, private, or hybrid route, moving to the cloud is a very popular decision—in fact, you’ll find 93 percent of companies share your strategy. Of course you didn’t adopt cloud because you wanted to jump on a bandwagon, you did it because of the myriad benefits this new type of data storage brings to an organization. But, how well did you assess privacy issues? What about the very real potential for a company security breach that results in the loss of sensitive data? Did you train your staff well enough? How confident are you that your shared documents are fully protected against a cyberattack?
Getting nervous? Don’t be. Anytime you relinquish even the littlest bit of control of some facet of your business for efficiency’s sake, you’re bound to experience a twinge of anxiety. But this isn’t a doomsday post. Instead, it’s one that should make you think. Cloud is definitely worth the risks. Take it from the horse’s mouth—I run a virtual company and take advantage of all that cloud computing has to offer daily, and I’ve frequently sung cloud’s praises in the past.
That said, digital security should never be “the elephant in the room.” And every company’s security concerns are going to be unique. To be proactive, it’s important to determine where you’re likely to be most vulnerable, and what you can do about it.
More Data, More Room for Error
I mentioned that a recent survey found 93 percent of businesses are adopting cloud. Of that figure, 88 percent are using public cloud, 63 percent are using private cloud and 58 percent are using a mixture of both (hybrid). That’s a lot of data being shared, and those percentages are projected to get bigger (see Figure 1 for a breakdown of current vs. future public cloud VMs to give you an idea).
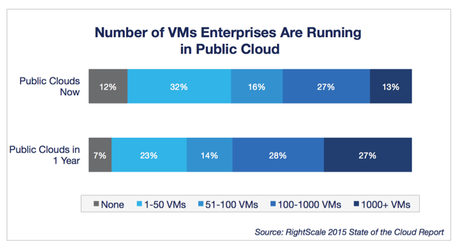
Figure 1: Number of VMs Enterprises are Running in Public Cloud. RightScale 2015 State of the Cloud Report.
To get to the point, storing more data in the cloud isn’t the problem, but more data allows for more room for error. Skyhigh Networks released a telling document, Cloud Adoption & Risk Report 2015 Q4, that found 15.8 percent of documents uploaded to cloud-based sharing services contain confidential information. Most of these (58 percent) are Microsoft Office documents, but PDFs, CAD diagrams, and JAVA code all made the list, too. Sensitive content being shared includes the following:
- Confidential company data like business plans, trading algorithms and source code (7.6 percent of files)
- Personally identifiable information like SSNs, tax IDs, addresses, and phone numbers (4.3 percent of files)
- Payment data like bank account numbers and credit card information (2.3 percent of files)
- Protected health information like treatment history, medical record IDs, and diagnoses (1.6 percent of files)
Many of these documents had incriminating keywords just in the filenames—words like “password,” “budget,” and “confidential.” I know what you might be thinking: What is the big deal if these documents are shared internally on a private cloud infrastructure (which they often are)? Isn’t that kind of the point of a private cloud? Well yes, but take a look at Figure 2 from Skyhigh’s report and you’ll see that 5.4 percent of those documents with private information end up sent in such a way that anyone with a link can view them. That means those documents containing payment data, health information, confidential company data, and personal information are only one mistake—one click—away from being public and unprotected.
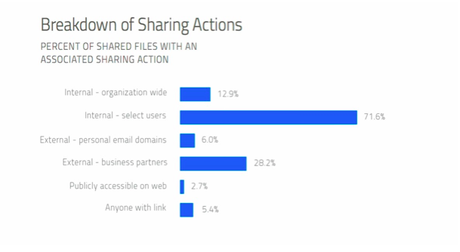
Figure 2: Breakdown of Sharing Actions, Skyhigh Networks
Compromised Cloud Accounts
Humans make mistakes, but those types of honest mistakes aren’t the only way sharing can lead to security breaches. If company credentials get compromised through database and/or phishing hacks (especially when we’re talking about SaaS applications), cyber-attackers gain access to all that private information while appearing to be legitimate users. This sticky situation can be difficult to detect and, unfortunately, isn’t all that rare: Skyhigh found three out of four companies they studied had at least one compromised account a month. See Figure 3 for the rest of their breakdown by threat type.
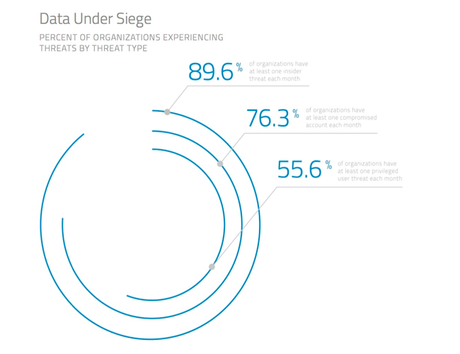
The Importance of Oversight
Part of the appeal of cloud adoption is its virtually endless potential to streamline processes and facilitate collaboration among various departments within a company. In the end, the business case for cloud is real—it can boost employee productivity and overall company efficiency if done correctly. What, though, is the role of the IT department in this ever-changing cloud climate? Oversight, oversight, oversight. (Did I mention oversight?) If accounting, HR and marketing all wish to dabble in some sort of cloud app to streamline workflow, it’s IT’s job to help leaders from those groups evaluate and select appropriate cloud solutions that meet their needs as well as comply with company policy. It’s also important to train individuals on what is and is not proper cloud etiquette when company data is concerned.
The last thing IT wants to do is “slow down” company productivity with extra training and red tape, but that’s a perception that we need to get past. The guidance and data restrictions are all part of a grander IT oversight that needs to be in place when sensitive company information is at risk, and taking the time to do it at the outset can save valuable time backpedalling later.
Forward Motion for Enterprise IT and Cloud Security
In-house IT departments don’t have to walk around with the weight of potential sharing mishaps on their shoulders. Now, some major players in the cloud space have built noteworthy new security features into their applications to help ease that burden. Take Dropbox for example, a staple for business file sharing. Just last month, they released “Dropbox Enterprise,” a new solution for companies that has built-in functionality that tracks what kind of sharing is happening, whether by employees, vendors, or clients. This is surely a move toward helping enterprise IT teams control the security dangers presented by sharing.
According to Dropbox’s blog, even HIPAA-regulated businesses can now use the service with the new security controls. That, in and of itself, speaks to the power of these built-in compliance oversight and security features.
Points to Ponder
Now, I hope you’ll see that those questions I posed when I started this post—those few inquiries about proper training, private data security and cyberattacks—were more about perspective and starting a conversation than about piquing your cyber-anxiety. If you were to reexamine your cloud adoption and usage, do you think you’d find a deficiency in staff training? A lapse in oversight by your IT department? If so, I challenge you to identify two or three actions you could take in the next quarter that could help address any areas of concern. The approaching new year is an opportunity to renew your focus on sharing, security and what they both mean to your business.
Let’s widen out this conversation. In a broad sense, what could enterprise IT be doing to better control the security dangers presented by sharing? Maybe it comes down to best practices. Perhaps built-in functionality, like that exhibited by Dropbox (discussed above), will become the norm on some share-heavy cloud apps. For many, I think feature that will be a huge selling point. What do you think? What would you like to see more of from cloud when it comes to security? As cloud becomes the norm for enterprise, how concerned are you about sharing and data loss in the long run? I’d love to hear your thoughts.
Additional Resources on this Topic:
What’s the Right Firewall Option for Cloud Security?
Cloud Security Risks: Is Your Industry Safe?
All Businesses Share the Same Cloud Security Concerns
This post was brought to you by IBM for MSPs and opinions are my own. To read more on this topic, visit IBM’s PivotPoint. Dedicated to providing valuable insight from industry thought leaders, PivotPoint offers expertise to help you develop, differentiate and scale your business.

