
Security has become an ever more important part of using a personal computer. Increasingly, the daily headlines include news of companies and websites getting hacked. It is important to learn how to properly secure your wireless Internet as well as secure your personal computer. This article focuses on how to secure your wireless network router so that you do not become part of the statistics. The wireless router typically includes a firewall that defines the perimeter of your network. Think of this as a fence, walling off your network from the Internet. Having a vulnerable wireless network allows criminals to possibly steal your data as well as Internet access. You could also become responsible for illegal downloading if your wireless Internet was compromised.
Cable or DSL Modem Direct Connection
Some high speed Internet connections allow you to directly connect your computer to the modem. We recommend installing a network router in this situation to help protect the computer from external traffic. Install a wireless router and turn off the wireless capability if you do not need it.
Hardwired Ethernet Network
Secure wireless is an oxymoron! Using a hardwired Ethernet connection is much more secure than wireless Internet, a must for those looking for the maximum protection. Unfortunately, this is type of access is not possible for some devices (iPad, iPhone, etc.) and is far from convenient. Most users who demand the utmost in security and performance lay Ethernet networking in their homes and businesses. They may still run a wireless network, but limit access on that network to just a couple devices.
Which Wireless Router Hardware?
Wireless router hardware is available from many major manufacturers, including Cisco – Linksys, D-Link, or Netgear. We suggest avoiding smaller companies because they may be slow to update the software (firmware) and patch security holes. Manufacturer’s models differ in wireless range, speed, wireless standard support (Wireless-N), and special features. Always make sure to update to the latest firmware available; bug fixes and enhancements were possibly added.
- Physical Location – Where you place the wireless router is very important.
- Position the wireless router to most central or optimal location for best coverage of your wireless network, and least amount of leakage to unwanted places like your neighbors or passersby on the street. This may be high up on a wall and may not be in the room the Internet connection is located in. Keep the wireless router away from microwave ovens and cordless phones.
- If you have sufficient wireless coverage and your wireless router supports it, you could also Reduce your wireless router’s transmitter power so it doesn’t send the signal beyond your home.
- Run a utility such as inSSIDer that helps you adjust your wireless router’s channel configuration to prevent interfering with surrounding wireless wifi networks. Wifi Analyzer for Android, Wi-Fi Finder iOS also works. Most routers are preset to channel 6, causing more collisions.
- Antennas – Low cost 3rd party add on antennas extend range without the need to buy a new wireless router; free antennas can also extend range. Some antenna’s omnidirectional, while others are directional, allowing you to focus a wireless signal. Replace the cheap antenna that came with your wireless router, to significantly increase performance.
- Add an electrical power timer to turn off the wireless router when not in use or at night. This saves money and offers added security.
Wireless Network Router Settings
Wireless routers need to be configured properly to ensure proper operation as well as maximum security. Although wireless routers from different vendors include differing configuration options, most include these configuration settings. We have included screenshots for a variety of popular wireless routers, but can never cover every single wireless router available. We recommend disconnecting your cable or DSL modem while your router is being configured as some routers take a while to boot up and present an unfiltered connection while loading up.
Before you make any changes to your wireless router, always note how it was configured before the changes were done, so you can undo changes.
Access the administrator configuration for your wireless router by either running the software that was included with it or by accessing it directly from a web browser. For instance, Linksys router security with their wireless routers can be accessed when entering the following URL into your browser: https://192.168.1.1/
Administrator Password
- Password entered to gain access to the wireless router hardware. The administrator password MUST be changed from factory default to something difficult and long. Many people never change the factory password and leave themselves wide open to getting hacked. See our article on generating secure passwords for tips.
- Disable remote router access or Remote management so no one can change your settings from outside your network. On Linksys routers, it is located on the Administration tab – Management.
- Enable Logs so that you can go back and see where problems arose.
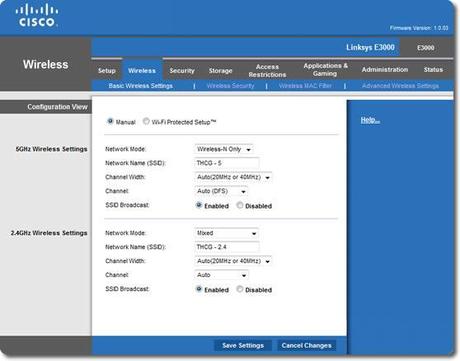
Cisco Linksys Wireless Security Settings
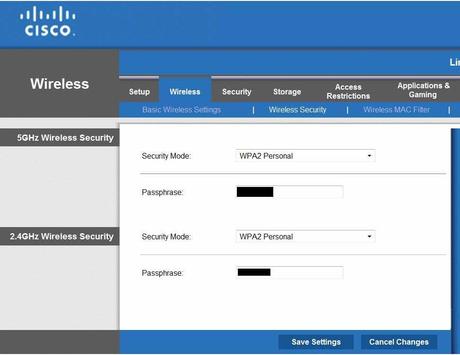
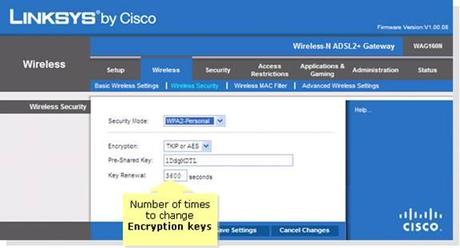
Cisco Linksys Dual Band 2.4Ghz 5Ghz Wireless Security Settings
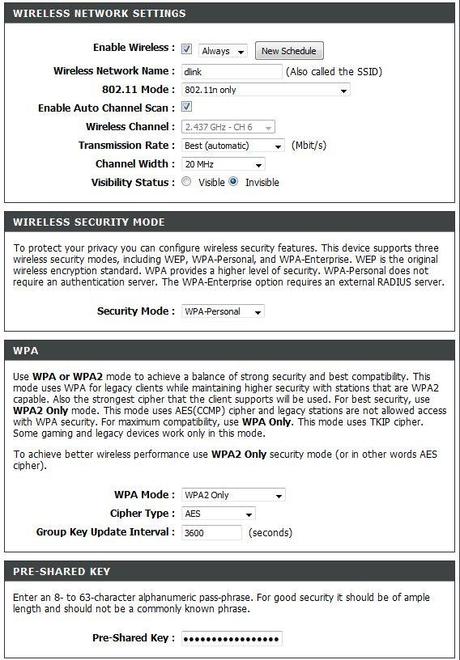
DLink Wireless Security Settings
Wireless Encryption
- It is best to use WPA2-Personal security mode, AES encryption (do not select TKIP), a long Pre-Shared Key. Recommendation: Long (40+ characters) and include symbols, and upper and lower case. You will have to enter this password on each wireless device.
- Do not use WEP or WPA encryption as they are easily hacked. WEP encryption can be broken in under a minute. If you have hardware that does not support WPA2 encryption, replace the hardware.
- Always use encryption and NEVER have an open Wi-Fi access point without a password.
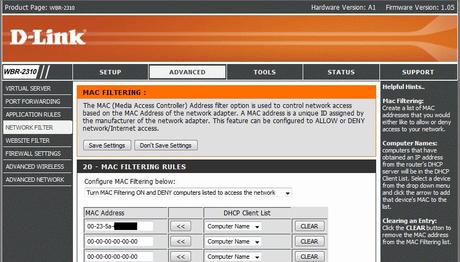
Mac Address Filtering
- This should be Enabled. This ensures that only authorized Wireless devices’ Mac Address (the serial number of the networking devices) are allowed to access the wireless router. Compile and enter a list of Mac Addresses from each device (computers, tablets, iPhone, smartphones, video game consoles, printers, etc.) and enter into this list. Consult your device’s manual or do an Internet search on how to find the Mac Address of a device. Set the wireless router to only allow access from devices on the list.
SSID
- Name – Change the default name. Do not use your address or a personal name. It is important to have a unique name so that when you’re away from home, your devices do not automatically try to logon to other wireless networks with the same name. Make sure you do not use names like: linksys, netgear, attwifi, 2wire####.
- Broadcast – Should be disabled to present easy access. You must manually enter the SSID name to connect to the network. This will make your network more invisible to the public. This does not make it anymore secure against hackers.
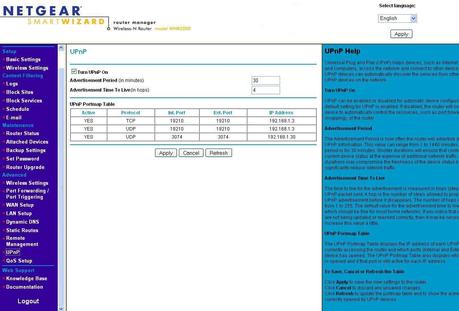
UPNP – Disable this feature. It makes your network much more vulnerable. Although adding devices will require manual action. You could also enable Universal plug and play only when adding a new device.
Wi-Fi Protected Setup (WPS) – Disable this feature (if possible) and enable manual setup, even though it makes setup much easier. It makes your network much more vulnerable to external hacking. A flaw allows a remote attacker to recover the WPS PIN and, with it, the router’s WPA/WPA2 password in a few hours was uncovered in December 2011. Checkout our WPS article on this.
Some older Linksys routers have SecureEasySetup™ (SES), which can be disabled to increase security.
Bands – More advanced wireless routers operate on multiple frequencies at the same time.
- 2.4 GHz – This is the typical Wi-Fi frequency used by most wireless routers.
- 5 GHz – Only advance routers support this frequency. Your computer or Wi-Fi device needs to also support the 5 GHz frequency option, so an extra network adapter may be required. Utilizing only this frequency helps prevent your network from being probed by less sophisticated hackers. *Note* 5 GHz performance transfer rate decreases dramatically the farther the device is from the router.
DHCP
- DHCP is used to handout Internet IP Addresses to your local network devices. Be sure to set a limit to the number of DHCP addresses given out by your router. This number should correspond to the actual number of devices you own. Occasionally, login to your router and audit the number of DHCP addresses given out, to look for nearby Internet leeches. RogueScanner is a free tool that will help you find rogue wireless access points and devices.
Wireless Routers with Guest Network
If your wireless router is capable of setting up a separate network for your Guests, you need to ensure that it is set up properly to prevent access to your main network. Keep in mind that some guest networks (Linksys, Cisco) simply have a password but do not utilize wireless encryption such as WPA2.
If you have a D-Link wireless router, be sure that the Enable Routing Between Zones option is not checked. This will prevent access by a guest onto your main network.
Additional Security
- Options such as Radius Authentication may be supported by the wireless router. This is more for corporate or small business security. ZeroShell allows you to set up a RADIUS server inside a virtual machine.
Third Party Wireless Router Firmware
- 3rdParty Firmware or software for the wireless router is often available with additional features not available from the manufacturer’s firmware
- Why? – Need a particular special feature. Often only for power users.
- What features would be available? – Stability, security, configurability
- Wireless Router Compatibility – Check website to see if your wireless router is supported by 3rd party firmware
- Tomato – Popular 3rd party replacement firmware for many wireless routers.
- DD-WRT – Popular open-source 3rd party replacement firmware for many wireless routers. This firmware enables you to adjust the transmit power of the router to help boost range.
Buffalo makes wireless routers with DD-WRT pre-installed. This allows them to reduce the amount of software (firmware) they have to write, and concentrate their efforts more on hardware. If you are afraid of accidentally damaging your wireless router by installing 3rd party firmware consider purchasing a Buffalo High Performance wireless router.
- Do It Yourself (DIY) Wireless Router – allows for advance features , good if you have extra computers, higher performance needs, QoS, IP filtering, traffic stats, special network configurations that are not mainstream.
- Smoothwall – Popular 3rd party Linux based router software. Runs on any Pentium-class PC with at least 128 MB of RAM. Snort Intrusion Detection System support is also available, so you do not have to run Snort in a separate installation.
Testing Wireless Router Security
Testing wireless router security is important to see how secure your wireless router really is. Here are some sites that help test your wireless router’s security. You can adjust your configuration to close any vulnerabilities they find.
- Rapid7 – Has penetration testing software
- Shields Up – Tests your network with tools from Steve Gibson of GRC.
- HackerWatch – Tests your network with tools from McAfee.
- HackerTarget – Multiple tests on your network
- Arachni – Security scanning framework
By applying special settings to your wireless router, you can significantly increase the security of your wireless network to prevent theft and secure our privacy.
This concludes our How to setup a Secure Wireless Network Router article. Other articles on Safegadget.com help you secure the other aspects of your personal computer, including How to Set up a Secure wireless network Router, and How to Secure Internet Explorer article, or How to Secure Firefox Article. Please see our other articles on security tips for your e-mail, iPad, online banking, online shopping, smart phones, and more.
