 Data Breach Protection
Data Breach Protection
The growing rate of security breaches have placed a number of organizations in the spotlight, subjecting them to noteworthy financial losses and damaged reputations. In order to prevent the occurrence of a data breach, organizations require a robust security strategy that safeguards their data, devices and clients. Today’s enterprise technology leader is responsible for not only protecting the organization against advanced security threats but also its clients or customers against various malware and phishing attacks. Taking into account the shift to a mobile workforce with BYOD (Bring Your Own Device) becoming increasingly common in many organizations, the security risk factor is further complicated with the intricate mix of mobile apps and devices in the workplace.
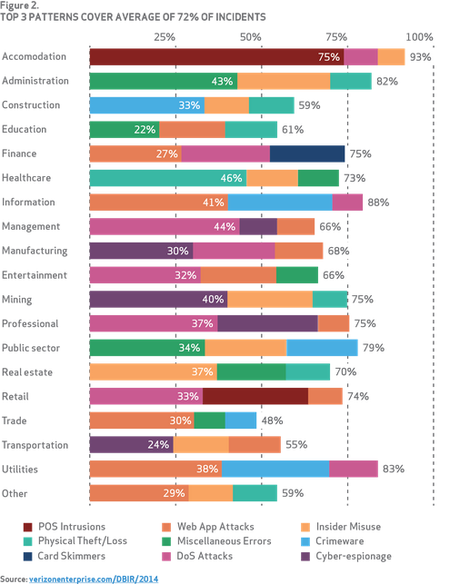
What causes the risk?
What pre-emptive measures should an organization undertake to reduce the risk of a breach?
Be aware of what personal information is available, where it is located, and what it is being used for. Data records and process maps can assist the organization in providing a blueprint of precisely what personal information needs to be protected (as well as when and where it needs to be protected). It’s important to first understand the data before it can be protected.
Recognize vulnerabilities. Conduct risk and vulnerability assessments and/or penetration tests within the organization to make certain that threats to privacy are detected. In addition to focusing on technical vulnerabilities, think about third parties associated with the organization. For example, are third parties gathering personal information on the organization’s behalf without suitable security measures? Does the organization utilize paper-based application forms, which are then passed on to a central location (the loss of which may result in no way of identifying who the affected individuals are, or even how to inform them)? When an upgrade is conducted, do the old systems and databases stay active, unmonitored and unpatched?
Create a data breach notification policy/procedure: Creating a data breach notification policy will let clients or customers know what steps the organization will undergo if an attack transpires, while at the same time making certain that the correct procedures will be taken.
Coach IT personnel: IT personnel accountable for securing the organization’s network should be educated on how hackers operate and how to recognize a data breach.
Institute organization policies: To reduce the threat of an attack, all staff should have a good knowledge of what tools, devices and networks are permitted to be utilized and in which circumstances they should be used. It is crucial to train all staff in the organization on the security and regulatory risks associated with utilizing tools outside of company policies.
Apply an enterprise collaboration solution: To facilitate the organization to cooperate freely and securely, consider a file sharing solution that builds on existing solutions, places the end user first and does not compromise on security and control.
Uphold regulatory requirements: To make certain the organization’s procedures are compliant, it’s crucial to work with the security and legal departments to fully comprehend the regulatory environment.
Develop a solid Incident Response Plan. It’s essential to construct an incident response plan in advance, prior to the occurrence of a breach. Some questions to consider include: what is the organization’s communication plan? Who should be notified in case of a possible breach? What information should board members be aware of? What should the organization tell its clients or customers?
Taking these precautionary steps to safeguard against threats will help to ensure that your organization remains protected against potential future attacks.
The Litcom Approach
Today’s business leaders wonder how secure their organizations and IT systems are, and often struggle to find the right strategy to balance implementing effective information security controls and achieving business objectives of cost reduction and agility. Litcom provides information security expertise and skilled resources to assist our clients in a variety of information security capacities including:
Health Check
The security health check provides a comprehensive yet attainable tool that will evaluate critical elements of your information security including:
-
Information Security Strategy – Understand how information security should enable your business, and determine whether or not an effective security strategy is in place.
-
Security Management and Governance – Evaluate if you have the right organizational and policy structures to support your information security function(s).
-
Security Operations – Verify the adequacy of incident response, identity and access, and vulnerability and risk management processes.
-
Privacy and Compliance – Evaluate your privacy and data protection processes and mechanisms in order to strengthen your regulatory compliance.
-
Technical Architecture – Assess technical and logical controls (e.g. network, application and security tools) resilience against cyber and internal threats. Optionally, this may also include technical vulnerability assessments and penetration testing.
Program Management
Litcom will help your organization develop an information security program that is effective, adequate to your organization culture, and cost effective. We offer professional consulting services for organizations to select, plan, and implement information security products and solutions in areas such as: Security Information and Event Management (SIEM) technologies, Intrusion Detection and Intrusion Prevention Systems (IDPS), Identity and Access Management Solutions (IAM), Security Architecture and Design. We help our clients progress through the various selection stages from requirement definition, to development of Request for Proposals (RFP), to vendor evaluation and contract negotiation, and to project management and implementation. For more information on our security services, please contact us at: [email protected].
Sources:
http://www.verizonenterprise.com/DBIR/2014/
Stay Connected
265 Rimrock Rd., Suite 202
Toronto, Ontario M3J 3C6
phone: 905 763 8900
fax: 905 763 8233
email: [email protected]
Recent Posts
- The value behind an ERP Health Check Assessment: Maximizing the return on your organization’s ERP system
- Taking pre-emptive measures: Is your organization protected against a data breach?
- Looking forward to 2015: Why Outsourcing your IT may be the best bet
