 Every day it seems as though there’s another hacking story in the news, the most recent of which is yet another hacking by the Chinese of the federal government’s databases, this time gaining access to personal information on some four million current and former federal employees. Troubling, to be sure. More troubling if you happen to be an IT pro in the utility field charged with keeping your utility management system secure from hackers. Nobody takes news of security breaches lightly, and when breaches of this size and nature happen, utility management system pros know that there’s nothing more important than keeping their systems as secure as possible.
Every day it seems as though there’s another hacking story in the news, the most recent of which is yet another hacking by the Chinese of the federal government’s databases, this time gaining access to personal information on some four million current and former federal employees. Troubling, to be sure. More troubling if you happen to be an IT pro in the utility field charged with keeping your utility management system secure from hackers. Nobody takes news of security breaches lightly, and when breaches of this size and nature happen, utility management system pros know that there’s nothing more important than keeping their systems as secure as possible.
The Cybersecurity Market and the Rise of Incidents
Increased risks, increased exposure, and a world driven by ever-changing technology means that the cybersecurity market is expanding at a rapid rate. According to the Wall Street Journal, research firm Gartner predicts that global IT spending on security is expected to reach 76.9 billion in 2015. Probably not a surprise to anyone in the IT field, is it?
Why so much spending on security? Respondents to The Global State of Information Security Survey 2015, more than 9,700 security, IT, and C-Suite executives reported some 42.8 million security incidents detected, which is an increase of 48 percent over 2013. And that’s only a 66 percent year-over-year increase of the compound annual growth rate of security-related incidents since 2009. Ever wonder why IT pros have insomnia? Oh wait, you know why!
The Dangers of a Breach for Utilities
So we know security-related incidents are on the rise, let’s think about the dangers associated with an attack on our utility infrastructure. We know that consumers take for granted services like water, power, transportation networks, Internet networks, oil and gas pipelines and the like. And the failure of any one system could potentially have a much broader, infinitely more catastrophic impact on many other systems. I like how Robert Bea, a risk assessment expert and professor at UC Berkeley, explains this: “Should one piece of a system fail, you end up with these cascades, sort of a like a game of dominos. It doesn’t take anything horribly catastrophic to initiate an infrastructure disaster. Using cyber-attack methods, individuals with malicious intent could determine the most efficient way to trigger multiple infrastructure failures.” He used Hurricane Katrina, and the infrastructure failures that plagued New Orleans for what was, in many cases, months and even years after the hurricane, as an example of the commonalities between a natural disaster and an infrastructure breach.
Protecting Your Utility Management System From Hackers
There are some fundamental ways to keep your utility management system safe; let’s talk about the four steps you can immediately get your arms around:
- Humans are, by and large, the greatest threat to security. They don’t know what they don’t know, and expecting them to be inherently risk aware is, well, naïve at best. Your employees and contractors are very often uneducated about basic security steps that all with access to any utility management system need to be aware of. Regular and on-going training, and a focus on educating both employees and all contractors with any and all access to your utility management systems on the basics principles of security is key. It’s important to remember that training is not an event, it’s a process, and in order for it to be effective it’s got to be a part of your team’s daily work routine.
While we’re on the topic of humans, it’s also important to point out that from the outside looking in, it’s easy to think that outsiders are responsible for the majority of the security breaches experienced by businesses today. That’s not really the case. Here’s a graphic from the PwC Global State of Information Security Study that shows there’s likely more threat of security incidents and breaches occurring related to current employees, former employees, and current service providers/consultants/contractors (all of which are on the rise) than there is from hackers.
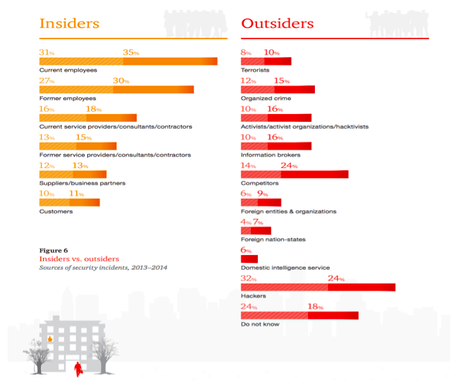
Know Your Weaknesses. Multiple areas of weakness exist within any organization—and that’s more true today (for utilities as much as any other business), in the world of BYOD and social networks, and a mobile workforce, than ever before. Make sure that you’re factoring in all potential areas of attack, including passwords, mobile devices, social networks, email, targeted phishing schemes, and vendors or contractors with access to your facility and/or your utility management system at any time. Also, as many of you know, online bill pay presents its own network security issues and when you can utilize solutions that can detect and get rid of malicious traffic in real time as well as deliver the compliance you need, it’s a huge bonus.
- Fire Drills. You can do all the training in the world, but if your team doesn’t know how to operate when the real deal happens, you’ll be in a world of trouble. Make sure that fire drills, or mock cyber attacks, are part of your ongoing security training and protection measures. During these mock attacks, that’s when your team will have the greatest opportunity to not only think on their feet, but to learn as part of the process.
- Data to the Rescue. So you’ve embraced the concept of training, and run routine mock cyber attacks as part of your standard operating practices. Now data can, and should, play a role in your security operations. What you need to do is to use the data you’ve collected as a result of these steps to analyze and monitor where your team is on the completion of training assignments, as well as their individual performance as part of the team working on the mock cyber attacks. Continual internal performance testing, both on training capabilities as well as in full on crisis mode (even if it’s a mock crisis), is key when it comes to emergency preparedness and the ability to function extremely effectively when a crisis does actually occur. And make no mistake on this front, a crisis will occur—it’s not a matter of if, just a matter of when. What you’re doing when you’re developing your teams in this way—training, testing, using the big data capabilities that are available to you to gather and analyze that data, and then tweaking your operations using the results of that data—is you’re creating what could well be called a finely tuned firewall. And there’s a lot to be said for the logic of the firewalls in your organization being of a human nature.
Having a prevent and protect mindset when it comes to keeping your utility management systems safe only makes sense. Big data allows you to do that, and a focus on your human resources allows you to do that. I think that just about every CIO and IT pro would agree that it is far better to be proactive when it comes to cybersecurity than it is to be reactive. The only challenge when it comes to that is getting the budget dollars that you need in order to make that happen. To that end, in closing, maybe this graphic from The Global State of Information Security Survey will help. Note that employee training is the highest on the list of top spending priorities of survey respondents—and for good reason.
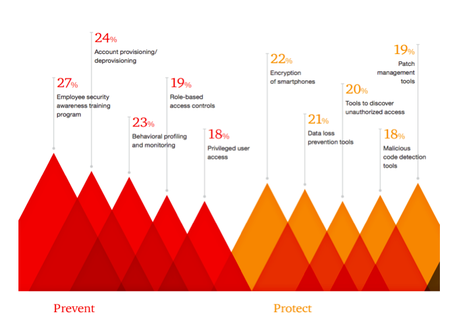
What do you think? What kind of training operations do you have in place? Are you doing your own fire drills, testing your team with mock cyber attacks? Has it helped with your preparedness and training initiatives? What’s in store for you and your team for the remainder of 2015? I’d love to hear your thoughts on this.
Other Resources On This Topic:
Crashing the System: How to Protect Critical Infrastructure from cyber attacks
Keeping the Electric Grid Safe From Attack
Eastern Maine Electric Cooperative (EMEC) Utilizes Dell SecureWorks for protecting enterprise and payment systems
This post was written as part of the Dell Insight Partners program, which provides news and analysis about the evolving world of tech. For more on these topics, visit Dell’s thought leadership site Power More. Dell sponsored this article, but the opinions are my own and don’t necessarily represent Dell’s positions or strategies.
photo credit: Infrastructure via photopin (license)

